Split tunneling vs. full tunneling: Which should you use?
A virtual private network (VPN) can be configured to handle your traffic in two modes: full tunneling and split tunneling. With full tunneling, all your traffic goes through the VPN, whereas with split tunneling, you choose what traffic to send through the VPN and what traffic can take the regular internet route.
The mode you pick influences how private your activity remains, how much speed you keep, and whether certain apps or services can run without issues. It’s a trade-off that matters in practice, not just on paper.
In this guide, we break down how full and split tunneling work, the compromises that come with each, and how to choose the option that fits your needs best.
What is split tunneling?
Split tunneling lets you route some of your traffic through the VPN while sending the rest directly over the internet. Consumer VPN apps usually let you pick this on an app-by-app or website-by-website basis.
The feature exists for compatibility and performance. With a full tunnel, some services fail because they reject traffic from VPN IP ranges, require a home-country connection, or need access to other devices on your local network, such as printers, file servers, or smart TVs.
Sending all traffic through a distant VPN server also means every packet is encrypted and relayed before it reaches its destination. That extra step can slow things down, especially for users far from the server. That said, top-tier VPNs like ExpressVPN keep this speed loss to a minimum.
How does split tunneling work?
When you enable split tunneling, the VPN client installs routing rules on your device. These rules decide how each connection is handled. Every time you open an app or website, the VPN checks whether that traffic should go through the encrypted tunnel or bypass it.
- If a rule says to use the VPN, the connection is encrypted and routed through the VPN server at your chosen location.
- If a rule says to bypass the VPN, the connection skips encryption and goes out normally through your internet provider.
Once configured, this happens automatically in the background. In most consumer VPNs, you can choose which apps or websites follow which path.
Behind the scenes, VPN clients also handle the data encryption and encapsulation process that keeps your tunneled traffic private. If you’d like to see a deeper breakdown of how VPNs secure your data, check out our guide to how a VPN works.
Types of split tunneling
VPNs implement split tunneling in various ways. The setup you choose depends on whether you want to include only a few apps, exclude a few apps, or control routing at a network level.
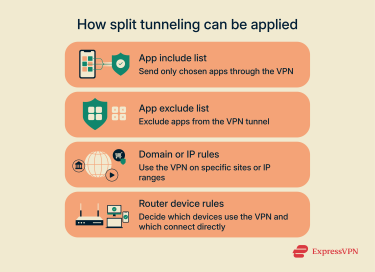
App include list
You specify which applications should use the VPN. For example, your web browser and email client can remain inside the tunnel while other apps connect directly. This is also called inverse split tunneling, and it’s useful when you only need encryption for a handful of programs.
App exclude list
Instead of choosing what to protect, you choose what to bypass. Everything except the apps on your list stays inside the VPN. Many people use this when most of their traffic should be secured, but they want some services and apps to connect outside for better compatibility.
Domain or IP rules
Some VPNs allow split tunneling at the destination level. You can configure specific websites or IP ranges to use the tunnel, while others go direct.
Device groups on a router
When a VPN runs on a router, split tunneling can be applied at the device level. Instead of configuring each app, you decide which devices use the tunnel and which connect directly.
What types of split tunneling does ExpressVPN offer?
ExpressVPN supports split tunneling across different modes and platforms. Android users can split-tunnel by app. On Mac (macOS 11 and later) and Linux, split tunneling includes a more advanced option that lets you add or remove both apps and IP addresses from the VPN tunnel.
On Windows, you can choose which apps, IP addresses, or subnets go through the VPN and which stay direct. On routers, you can use the Device Groups function to choose which devices connect to the VPN and which don’t (and customize other settings).
Benefits of split tunneling
The biggest advantage of split tunneling is flexibility. Instead of choosing between complete protection and no protection, you can tailor the VPN to your situation.
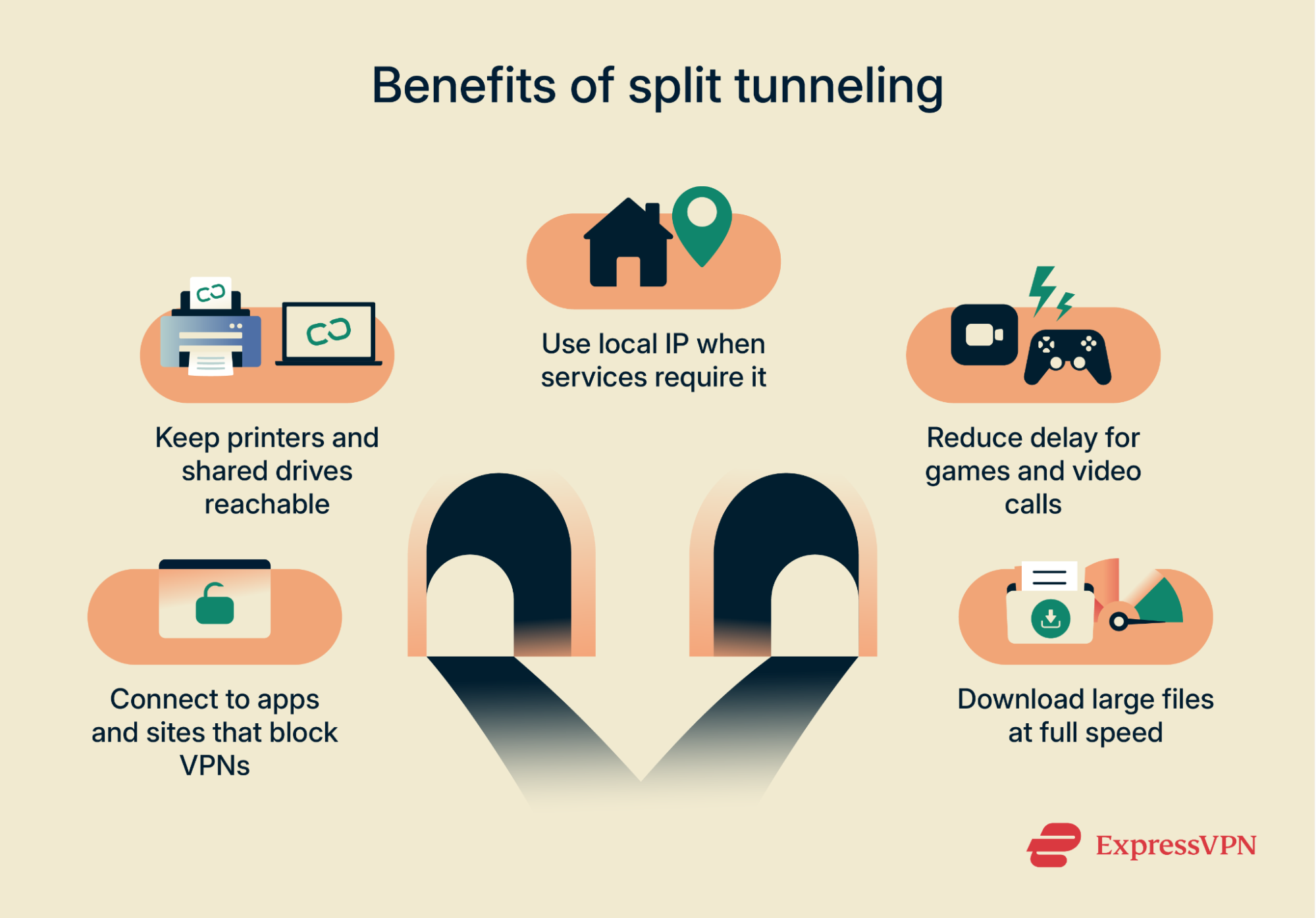
Avoid blocked services
Some sites, such as banks or government sites, refuse connections from VPN servers. Split tunneling lets those apps connect directly while the rest of your traffic stays encrypted.
Keep access to local devices
Printers, shared drives, and smart TVs remain reachable when only selected traffic is sent through the VPN.
Reduce latency for real-time apps
Games, video calls, and other latency-sensitive tasks generally perform better when they bypass the tunnel instead of routing through a distant server.
Maintain speed for large downloads
Updates, backups, and other heavy transfers can run outside the VPN at full internet service provider (ISP) speed, leaving the tunnel free for activity that needs protection.
Security risks and considerations
Split tunneling can solve compatibility problems, but it also creates security risks that full tunneling avoids. The main risks are:
- Unprotected traffic: When you route an app outside the tunnel, its data travels like any normal internet connection. On unsecured public Wi-Fi, that information can be captured by others on the network in a man-in-the-middle (MITM) attack, and over a home or mobile connection, it’s visible to your ISP.
- Domain Name System (DNS) exposure: Apps you exclude from the tunnel still need to look up the addresses of the sites they connect to. This process (called DNS resolution) turns a domain name like example.com into a numerical IP address. If the lookup happens outside the VPN, it goes to your ISP or another DNS service you’ve set, and they can see which sites you’re visiting.
Best use cases for split tunneling
Split tunneling is most valuable when you need the VPN for certain tasks, but a full tunnel would break connections to important services or slow down work. A few situations stand out:
Remote and hybrid work
Employees may want all their browsing traffic protected by a VPN, but they still have to connect to local resources like printers or other local devices. Split tunneling lets the business traffic flow through the VPN while the rest stays on the regular connection.
Users on restrictive networks
On networks where some sites or services are blocked, split tunneling lets you send just the restricted traffic through the VPN while leaving the rest direct. This avoids slowing down routine activity that doesn’t need the VPN.
Using location-restricted services alongside private activity
Some services (like banking websites or government portals) check your IP address location before granting access. At the same time, you may want other traffic, like streaming or gaming, to stay inside the encrypted tunnel. Split tunneling allows you to keep sensitive activities protected while letting location-dependent services connect directly through your regular internet.
Managing slow connections
On weak Wi-Fi or mobile data, a VPN can make an already slow link feel even slower. Split tunneling helps by keeping only sensitive activities (such as logins or private browsing) inside the tunnel, while the rest of your traffic uses the open internet directly.
What is full tunneling?
Full tunneling is the default mode in most VPNs. Instead of letting some traffic go direct and some go through the VPN, everything from your device is sent through the encrypted tunnel. Apps, background services, and system processes all follow the same path.
How full tunneling works
When you connect in full-tunnel mode, the VPN changes your device’s network settings so that all internet traffic is routed through the tunnel. The VPN client encrypts that traffic locally before it leaves your device, sends it to the VPN server, and from there it is forwarded to the site or service you’re trying to reach. Because every connection follows the same path, nothing goes out directly, and to the outside world it all appears to come from the VPN server’s address.
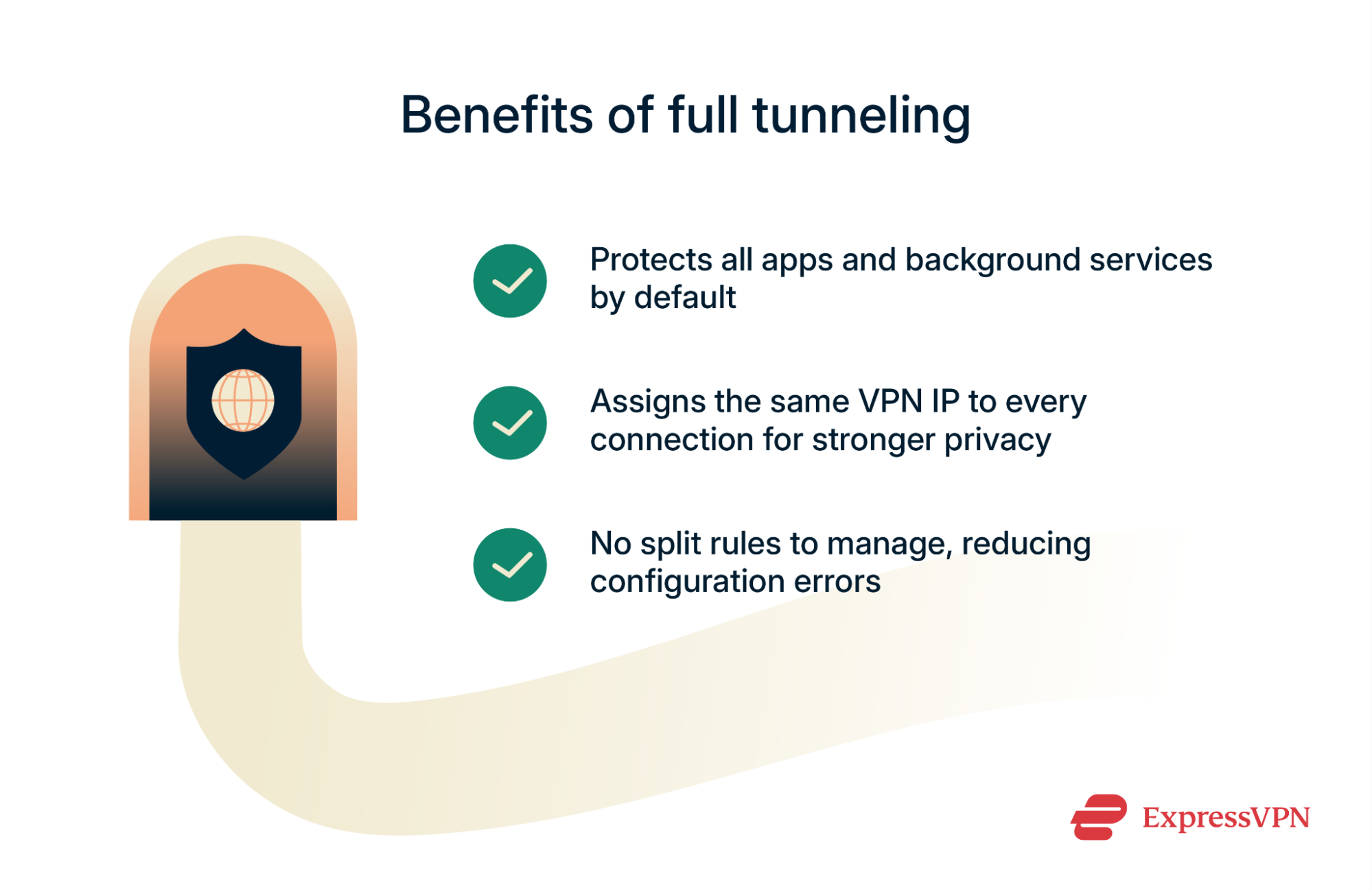
Benefits of full tunneling
- Complete protection: All apps (including background services) are encrypted by default. There is no need to configure rules or worry about missing something.
- Stronger privacy: Every connection shares the same VPN IP, which makes it harder for websites or services to trace your online activity back to you.
- Simplified management: Because there are no split rules to maintain, there is less chance of mistakes such as leaving sensitive apps or domains outside the tunnel.
Potential drawbacks
Full tunneling eliminates gaps in coverage, but it comes with costs you notice in daily use.
- Added delay: Every connection is encrypted and sent through the VPN server before reaching its destination. If the server is far away, or if the connection is already slow, pages load and apps respond more slowly than they would on a direct connection (even the ones that don’t need protection).
- Service limitations: Some banks, streaming platforms, and government portals reject traffic from VPN endpoints. With full tunneling, you can’t make exceptions for those services. The only workaround is to turn off the VPN entirely when you need them.
Best use cases for full tunneling
Full tunneling is suited to environments where leaving any traffic outside the VPN would create risk or break policy. These include:
Public and untrusted networks
A traveler connecting from hotel Wi-Fi or an airport lounge, for example, has no visibility into who runs the network or how it is secured. Full tunneling ensures that every app and service on the device is protected, with no exceptions left exposed on the open network.
Monitored environments
In workplaces, universities, or countries where internet traffic is filtered or logged, full tunneling prevents unencrypted connections from leaking. It forces every service to use the encrypted path, keeping activity private even when local monitoring is in place.
Privacy-first setups at home
People who want maximum privacy use full tunneling on all of their devices: laptops, phones, and even home setups like smart TVs routed through a VPN router. The advantage is consistency: every connection, no matter the app or device, is treated the same way and protected by the VPN.
Split tunnel vs. full tunnel: Key differences
Here’s how these two tunneling methods differ in key areas: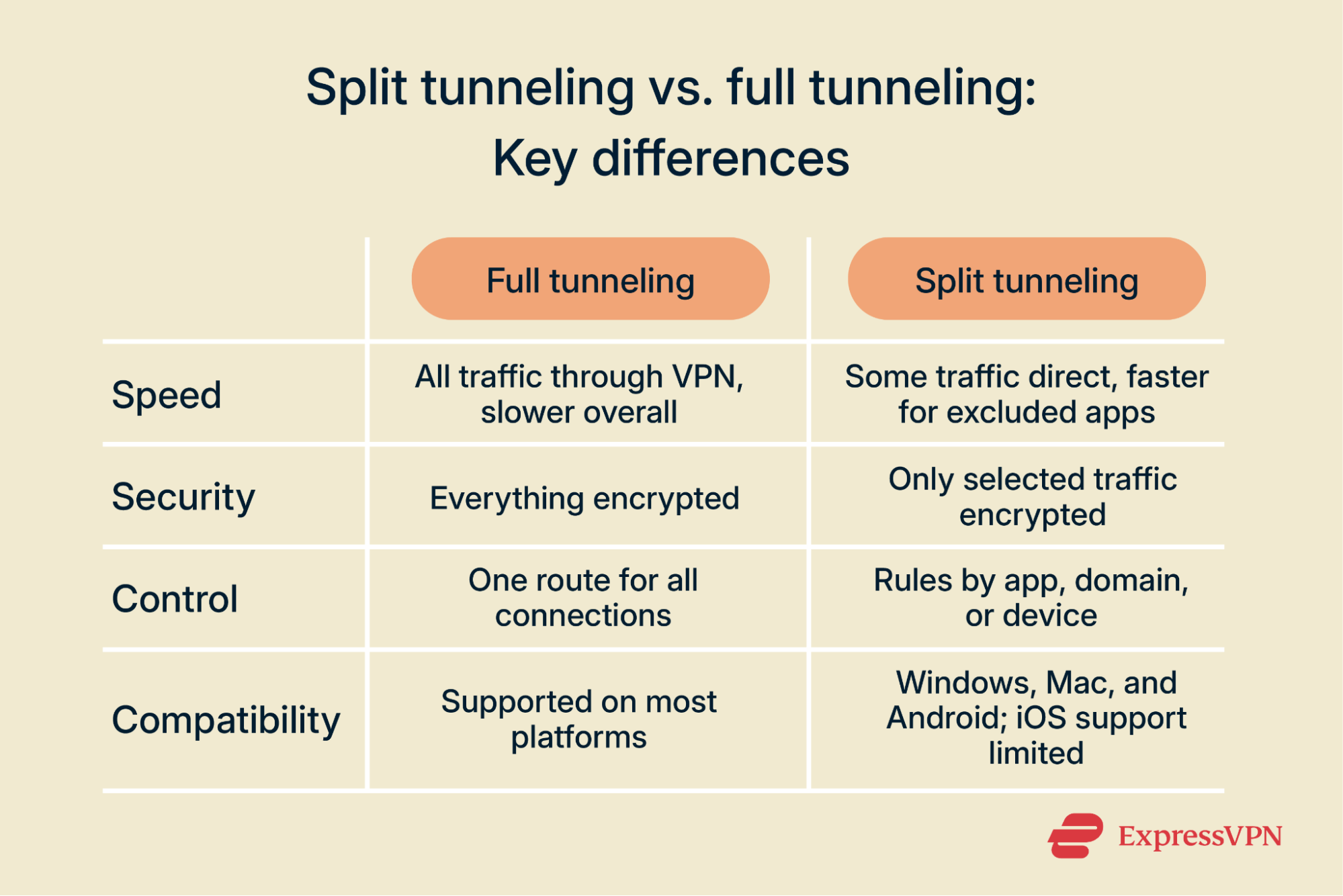
Speed and latency
Full tunneling runs everything through the VPN server, which adds an extra hop. The encryption step and the longer route can slow things down compared with a direct ISP connection.
Split tunneling creates two paths. Traffic that stays in the tunnel behaves the same as it would under full tunneling. Traffic sent outside uses the open internet directly, which means faster response times and higher download speeds for those excluded apps.
Security trade-offs between the two tunneling methods
With full tunneling, all traffic is encrypted and sent through the VPN. Split tunneling lowers that protection, because anything left outside the tunnel travels as a normal connection.
That means that your IP address isn’t masked, the sites you visit are revealed through DNS lookups (unless you use DNS encryption), and excluded traffic becomes visible to your ISP, the local network, or attackers on public Wi-Fi. It also increases the chance of ad tracking.
Traffic control and routing flexibility
Full tunneling treats all traffic the same. Every connection follows one route through the VPN, which leaves no room for exceptions and removes user choice.
Split tunneling allows granular control. Routing can be set per application, per domain, or even per device when the VPN runs on a router. This lets users decide where encryption is applied and where it’s not.
Device compatibility and platform limitations
Full tunneling is widely supported. On most operating systems, once the VPN client connects, all traffic can be routed through the tunnel without extra setup. This consistency is why it remains the default mode in nearly all consumer VPN apps.
Split tunneling is less consistent. Support depends on both the VPN provider and the platform. Desktop systems like Windows and macOS, as well as Android, generally allow app-based split tunneling if the VPN client supports it. iOS is more restrictive and permits far fewer options.
ExpressVPN offers app-level split tunneling on Windows and Android; app- and IP-level split tunneling for Mac (macOS 11 and above) and Linux; and device grouping for routers.
How to choose the right VPN tunneling strategy
Both tunneling modes encrypt traffic, but they serve different goals. The right choice depends on whether you value full coverage, flexibility, or a balance of the two.
Privacy
If your top priority is privacy, choose full tunneling. Every app, background service, and system process uses the VPN by default. Nothing is left outside, which eliminates the chance of accidental exposure.
Speed and performance
If you want to maximize responsiveness for certain tasks, split tunneling may be a better fit. Full tunneling adds latency and can lower download speeds because every connection is encrypted and routed through the VPN server.
With top-tier VPNs like ExpressVPN, the difference on nearby servers is usually small, but it still applies to all activity. Split tunneling lets you exclude large downloads or latency-sensitive apps so they run at direct ISP speed, while any sensitive activity stays encrypted.
IP identity management
If you only need one public IP address, full tunneling is straightforward. Every app and service sees the same VPN server IP. If you need two at the same time, split tunneling makes that possible. One app can use your ISP IP to access home-country services, while another masks your ISP IP by connecting through a VPN server.
Compatibility with apps and devices
If you use network printers, file servers, or smart devices that depend on local connectivity, split tunneling keeps them reachable without disconnecting the VPN. Full tunneling, in contrast, can block that visibility.
Level of management
If you prefer not to adjust any settings, full tunneling is the hands-off option. If you want more control, split tunneling gives you flexibility without being difficult to use; most modern VPN clients make it as simple as selecting which apps or services you want included (or which you don’t).
Split tunnel vs. full tunnel for enterprise
In business environments, split tunneling can be applied with more control than most consumer VPN apps allow. Instead of picking apps or websites, administrators can set rules that route specific types of traffic through the VPN while letting other traffic go direct.
For example, some companies force internal domains (like an intranet site) or certain protocols (such as Voice over Internet Proocol (VoIP) calls) to always use the VPN, while everyday web browsing bypasses it. Administrators may require tunneling only for traffic to sensitive servers, while allowing general internet traffic to bypass it. Microsoft even recommends split tunneling for Microsoft 365 services to reduce latency and improve performance.
That said, split tunneling in business environments can create compliance gaps because not all activity passes through the corporate VPN server for logging and monitoring. It allows greater flexibility for mixed workflows, but it also presents more complexity in policy enforcement, since different categories of traffic are handled in different ways.
For this reason, some organizations configure their devices to use full tunneling by default. This guarantees that employee traffic passes through corporate gateways, where logging, filtering, and compliance checks are applied.
Enterprise security considerations and best practices
The model your business adopts will need to satisfy compliance rules, support security frameworks, and remain practical to manage across thousands of users.
Compliance support
In sectors like healthcare or finance, organizations must prove that sensitive data never travels outside monitored channels. Full tunneling helps by ensuring every employee connection is logged at the corporate gateway. Split tunneling complicates compliance, which is why it’s either disabled or limited to clearly defined, low-risk destinations that compliance teams explicitly approve.
Zero-trust network architecture
Zero trust assumes that no connection should be trusted just because it comes from inside the network. Full tunneling fits this model because it pushes all employee traffic through the VPN server, where the company can enforce checks. At that point, the system can confirm who the user is and whether the device meets security requirements and can limit access so people only reach the systems they’re allowed to use.
Split tunneling doesn’t align well with this model, because some connections fall outside the controlled environment. Where it’s permitted, it’s usually limited to local resources like printers or intranet sites, while all other services remain subject to full identity verification.
Performance monitoring and policy enforcement
Full tunneling can put extra load on company VPN servers and slow down employees, especially those working far from the server they’re assigned. IT teams need to monitor performance so the VPN doesn’t become a barrier to productivity and consider implementing VPN load balancing (distributing connections across multiple servers) to prevent slowdowns and downtime.
For organizations that allow split tunneling, the focus shifts to control and visibility: exceptions should be approved in advance, logged, and reviewed regularly so administrators can demonstrate which traffic is covered by the VPN and which is not.
FAQ: Common questions about split tunneling vs. full tunneling
Is split tunneling faster than full tunneling?
Split tunneling is faster for excluded apps because they connect directly through your internet service provider (ISP) without passing through the VPN server. The difference is most noticeable on heavier transfers or latency-sensitive apps. That said, with a top-tier VPN like ExpressVPN, the speed gap for everyday tasks may be too small to notice.
Does split tunneling slow down the VPN?
No, split tunneling doesn't make the VPN slower. It simply divides traffic into two paths, so tunneled traffic goes through the VPN connection while excluded traffic runs at direct internet service provider (ISP) speed.
Is VPN split tunneling good or bad?
Split tunneling isn’t good or bad on its own; it comes down to what you use it for. It’s useful when you need speed or local access, like reaching printers or playing games that don’t work well through a VPN. But it can create problems if you exclude apps that handle sensitive data, because that traffic then won’t have VPN protection.
Is split tunneling good for gaming?
Often, yes. Letting the game client run outside the VPN can reduce latency and lag, while you keep chat or other apps encrypted. The trade-off is less protection; if you’re worried about distributed denial-of-service (DDoS) attacks or you’re on a risky network, full tunneling may be the safer option.
Is split tunneling safe?
Split tunneling is safe when used carefully. The traffic you choose to exclude is no longer encrypted, so it can be observed by your internet service provider (ISP) or network operator. Sensitive activity should always stay inside the tunnel. ExpressVPN makes this easy with clear controls in its apps, so you can decide exactly what should and shouldn’t go through the VPN.
Can I switch between split and full tunnel?
In VPNs that support both, yes. You can turn split tunneling on or off, or just change which apps and sites are included. That way, you can run in full tunnel when you want everything covered, then flip back when you only need certain traffic to go through the VPN. ExpressVPN lets you toggle between split and full tunneling modes directly in its apps, and router users can assign different tunneling modes to device groups for even more granular control.
Does full tunneling affect browsing speed?
Usually a bit. Since all traffic goes through the VPN server, pages can load a bit more slowly than they would on a direct connection, especially if the server is far from you.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN