What is cybersecurity? A simple guide for beginners

Cybersecurity affects nearly every aspect of daily life. From the phone in your pocket and laptop on your desk to smart devices in your home, all rely on strong protections to keep you safe.
Without protections, attackers could potentially steal your personal details, drain your bank accounts, or cause serious disruption. That’s why cybersecurity experts are always working on new defenses to keep both people and businesses protected from evolving threats.
Still, cybersecurity isn’t only about specialists and complex systems. It also depends on simple habits, practical measures, and tools that anyone can use. This guide explains what cybersecurity really means and outlines how to protect yourself from today’s most common online risks.
What is cybersecurity in simple words?
Cybersecurity is all about protecting computers, networks, and data from unauthorized access, damage, or disruption. As the number of connected devices, ranging from phones and tablets to Internet of Things (IoT) gadgets and appliances, continues to grow, so does the number of potential targets for cybercriminals.
In today’s world, where nearly everything runs on computers and smart devices, strong protection is more important than ever. Without it, individuals and organizations risk falling victim to data breaches, ransomware, fraud, identity theft, interception of sensitive communications, and other serious threats.
Types of cybersecurity explained
Cybersecurity is a broad term that encompasses several principles, including the software used to protect devices, the types of network defenses, and knowledge of safe cybersecurity practices.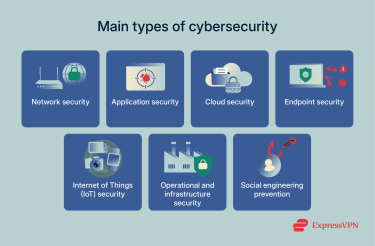
Network security
Network security protects your network from harm. Firewalls act as barriers that filter traffic and block unwanted connections, while access controls make sure only authorized users and devices can connect. Virtual private networks (VPNs) encrypt your internet traffic and mask your IP address, and monitoring tools keep watch for suspicious behavior so administrators can respond before attackers gain a foothold.
Application security
Application security ensures that software can’t be used as a gateway into sensitive systems. It includes both detection and response systems. Developers fix coding bugs, apply secure configurations, and test for vulnerabilities to ensure their applications are properly protected.
Cloud security
Cloud security protects data stored with third-party providers, ensuring that sensitive information remains safe even when it isn’t tied to a user’s own hardware. It combines technologies, policies, and controls to safeguard cloud-based resources from unauthorized access, data breaches, and service disruptions.
Many providers offer built-in defenses such as encryption, access controls, and monitoring tools, but users are also responsible for configuring their own security measures. This shared responsibility model means organizations must carefully manage account permissions, secure APIs, and ensure compliance with privacy regulations when moving workloads to the cloud.
Endpoint security
Endpoint security focuses on individual devices such as laptops, phones, and tablets. Because endpoints are often the first point of contact for attackers, protecting them reduces the chances of a compromised system. Antivirus, endpoint detection and response (EDR), and multi‑factor authentication (MFA) help block malware and unauthorized access.
Internet of Things (IoT) security
IoT security addresses connected devices, such as cameras, fridges, and various appliances. Many of these devices have limited built-in defenses, which makes them vulnerable. Using strong authentication and security software when possible, and updating the firmware, reduces the chances of an attack.
Operational and infrastructure security
Operational technology includes industrial control systems and automation devices that manage physical processes. Protecting these systems requires isolating control networks, monitoring old equipment and the network for strange activity, and securing the systems used in industrial processes.
Social engineering prevention
Social engineering relies on tricking people into revealing information or performing risky actions. Attackers will impersonate colleagues, support staff, government officials, celebrities, or companies. Prevention tactics include tools such as antivirus programs with phishing protection, awareness training, and staying up-to-date on the latest types of social engineering scams.
Common cybersecurity threats you should know
Attackers exploit technology and human behavior in various ways. Understanding these common techniques helps people and organizations take preventive action.
Malware and ransomware
Malware is malicious software that infiltrates systems to steal data, disrupt operations, damage the system, or create backdoors for additional malware. They’re one of the main challenges in the cybersecurity industry.
Ransomware is a specific type of malware where a scammer encrypts your files and demands payment to restore access.
Phishing and spear phishing
Phishing uses deceptive emails or messages to solicit credentials or personal information. Spear phishing tailors the deception to specific individuals, making it more convincing.
Phishing attacks are typically carried out over communication platforms, such as email or social media platforms. The attacker will almost always reach out first, attempt to instill a sense of urgency or fear, and push you to share sensitive data without thinking first.
DoS and DDoS attacks
Denial‑of‑service (DoS) attacks flood targets with malicious traffic, typically fueled by botnets. This makes websites or services unavailable. Distributed denial-of-service (DDoS) attacks harness many compromised devices to amplify impact. Both individuals and organizations can experience DDoS attacks, and these attacks significantly damage your network and impede your activities.
SQL injection and NoSQL injection
Injection attacks occur when a web application passes user input directly into a database query without properly checking or “sanitizing” it. Attackers can exploit this to make the database execute commands the developers never intended, potentially exposing, modifying, or deleting sensitive data.
Structured Query Language (SQL) injection targets traditional relational databases, which organize data in tables with rows and columns. For example, an attacker might exploit a login form by sending specially crafted input that tricks the database into bypassing authentication. In real-world cases, attackers have intercepted data from airline or e-commerce websites this way, stealing customer names, email addresses, and payment details.
NoSQL injection affects modern non-relational databases (like MongoDB), which use flexible document or key-value structures. An attacker could submit a JSON-style payload in a login form that makes the database treat “any username and any password” as valid, bypassing authentication entirely.
Preventing these attacks requires developers to validate and sanitize all user input, use safe query methods (like parameterized queries or query builders), and follow the principle of least privilege for database accounts.
Advanced persistent threats (APT)
APTs involve highly skilled adversaries who infiltrate a network and remain hidden while exfiltrating data or sabotaging sensitive systems. They often use zero‑day exploits, social engineering, and custom malware in tandem to carry out attacks.
These threats can linger inside a network for long periods of time before being detected. APTs can lead to long-term malware infections, data theft, or financial loss. They frequently target sensitive infrastructure, like the healthcare industry.
Insider threats
Insider threats occur when employees or contractors misuse their legitimate access, whether maliciously or accidentally. During corporate sabotage, attackers can use their insider status to exfiltrate information and infect the network or individual devices with malware.
Some employees become insider threats after falling victim to a phishing scheme or being negligent and accidentally installing malware or giving away sensitive company information to a scammer.
Man-in-the-middle (MITM) attacks
A man‑in‑the‑middle attack (MITM) intercepts communications between two parties. Attackers can eavesdrop or modify messages without either side noticing. Unencrypted data can be easily read or modified by a skilled criminal, emphasizing the need for data encryption software.
MITM attacks often lead to data theft and further attacks. Small- to medium-sized businesses are particularly vulnerable.
Zero-day exploits
Zero‑day exploits target previously unknown vulnerabilities. Because no patch is available, these attacks can go undetected and cause a lot of damage, particularly to businesses. When a criminal first notices the weakness, it’s referred to as a zero-day vulnerability. The attacking process is a zero-day exploit.
Real-world examples of major cyberattacks
Real-world breaches highlight the consequences of weak defenses and underscore why cybersecurity is so important.
The Equifax data breach
In 2017, a software vulnerability at the credit bureau Equifax allowed attackers to steal personal data, including names and Social Security numbers, of around 147 million people. The breach led to lawsuits, executive resignations, and millions of dollars in settlements.
Yahoo’s mega breach
In 2016, Yahoo confirmed two data breaches that happened a few years earlier, later disclosing the breaches affected up to 3 billion users. Stolen information included security questions and backup email addresses, which could be used to launch additional attacks on customers. The breach resulted in a settlement worth $117.5 million.
eBay’s security incident
In 2014, cybercriminals used stolen employee credentials to access eBay’s user database. They gained personal information and encrypted passwords belonging to eBay customers. While the company stated that there was “no evidence of unauthorized access or compromises to personal or financial information for PayPal users,” eBay forced a company-wide password reset.
FriendFinder Networks data exposure
A vulnerability in 2016 allowed attackers to access FriendFinder Networks databases, exposing roughly 412 million user accounts. Many passwords were either in plain text or weakly hashed. The leak led to a wave of sextortion scams targeting users.
Benefits of cybersecurity for businesses
Investing in cybersecurity provides measurable benefits:
Cost savings and ROI
Preventive measures simply cost less than dealing with breaches. Regular audits, staff training, adequate cybersecurity infrastructure, and practiced incident response plans all help reduce the likelihood of facing a breach and can mitigate the damages if one does occur. Additionally, you can typically lower your insurance premiums by demonstrating due diligence.
Falling victim to a data breach is costly. Attacks can disrupt operations, lead to revenue loss, damage your brand’s reputation, or provoke costly government fines, particularly if you weren’t following regulations when the breach happened.
Improved operational uptime
Good security minimizes downtime. Backups, patching, and resilient infrastructure let organizations continue operations during attacks and can help them recover from attacks faster. This leads to substantially less profit loss during disruptions.
Strengthened brand trust and customer loyalty
Research shows that customers prefer companies that demonstrate proper security practices. Certifications and transparent policies build trust, while a data breach can completely destroy that trust. Deloitte’s Connected Consumer survey found that 64% of respondents would consider switching technology providers after an incident that diminished a provider’s trustworthiness.
Strong and transparent security practices increase customer loyalty. In more competitive markets, a reputation for being safe can be a deciding factor for potential clients.
Protection of sensitive data and intellectual property
Protecting proprietary information, trade secrets, and customer data safeguards your competitive edge and reduces legal risk. Strong cybersecurity measures help keep sensitive details secure, while proper classification and handling of intellectual property help ensure your company’s most valuable assets remain protected.
Common challenges in cybersecurity today
Cybersecurity teams today work in a constantly shifting environment, where keeping systems secure is harder than it used to be.
Evolving threat landscape
Attackers constantly change or develop new tactics. Ransomware and exploitation of unpatched vulnerabilities remain a constant problem, and new techniques like fileless malware and AI‑generated phishing scams help scammers automate aspects of their attacks and deliver attacks with a wider scope.
Shortage of skilled professionals
Demand for skilled cybersecurity professionals exceeds the current supply. Organizations are struggling to hire and retain qualified staff, and skills gaps hamper their ability to protect networks without trained experts. The 2024 ISC2 Cybersecurity Workforce Study estimates a global gap of around 4.76 million unfilled cybersecurity roles.
Complexity of IT environments
Modern organizations use on‑premise servers, cloud platforms, mobile devices, and IoT devices. This is also paired with a combination of in-house and remote workers.
Together, this creates a complex web of various services and tools that make it hard for outsiders to easily learn the systems and adapt. Managing disparate systems increases risk because it becomes harder to maintain visibility and enforce policies across all assets.
Shadow IT and remote work risks
Shadow IT is when employees use apps or tools that haven’t been approved by the company. It’s a growing risk in the era of remote work. While these tools can make tasks easier, they also open the door to security gaps because they bypass official protections. When IT teams don’t know what’s being used, they can’t secure it.
Encouraging staff to check with IT before adopting new tools not only strengthens security but also builds trust between employees and management.
Best practices to strengthen your cybersecurity
Simple everyday habits, like using strong passwords and keeping software updated, go a long way in reducing your chances of an attack and limiting its impact.
Use strong, unique passwords and multi-factor authentication (MFA)
Every account should have its own complex password, ideally containing 14–16 characters and a mixture of numbers, letters, and symbols. MFA adds a layer of protection by requiring a second verification method to log in to an account. This works for preventing unauthorized access even if a password is compromised.
Because managing dozens of individual passwords can be extremely difficult, consider using a secure password manager to safely store them. ExpressKeys lets you securely store unlimited passwords, credit card details, and notes across all your devices, and it can also alert you to data breaches or weak passwords.
Keep software and systems up-to-date
Make sure you apply security patches and updates immediately to fix known vulnerabilities. Keep automatic updates turned on where possible, as this reduces the chance of oversight and ensures that your systems and software are always updated to the latest security patch. Regularly reviewing and updating your configurations also helps you maintain a good security baseline.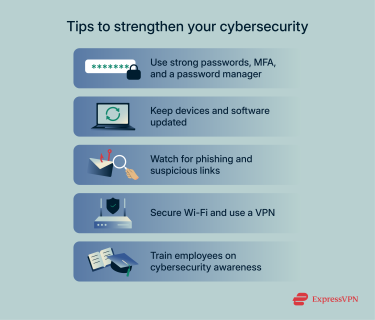
Avoid suspicious emails and links
Phishing attacks are very common, so you should be skeptical of unsolicited messages from any source. Always verify sender identities and avoid clicking unknown attachments. Report suspicious emails to protect other users or the entirety of your organization from falling victim to them. After this, promptly delete the message from any inbox it’s in.
Scammers will typically present an attachment alongside a call to urgency, such as a fake lottery winning or an emergency, or by pretending to be a trusted figure like a celebrity. Pay attention to shortened URLs, inconsistent website addresses, and awkwardly phrased messages.
Besides constant vigilance, using email filters and spam detection services helps reduce your exposure to malicious messages.
Secure your Wi-Fi and use a VPN
Changing your router’s default password and hiding it from view will decrease your chances of having your network attacked. You also need to make sure that your router is always updated to the latest firmware patch. However, you also need to encrypt your data; otherwise, a criminal could monitor your network traffic and use that to launch future attacks.
ExpressVPN uses a secure encryption protocol to wrap your data in a protected tunnel, preventing it from being readable. It includes a kill switch that automatically disables your internet if your VPN connection drops and a tracker blocker to restrict third-party tracking.
Learn more: Check out more ways to protect yourself online.
Cybersecurity tools and solutions
While personal best practices help individuals stay safe, organizations operate on a larger scale. They must protect entire networks, multiple devices, and sensitive customer or proprietary data. To meet these challenges, businesses rely on specialized tools that prevent, detect, and respond to threats across the organization.
Antivirus and endpoint protection
Organizations often use endpoint detection and response (EDR) platforms to monitor devices for malware and other threats. These tools provide real-time monitoring and allow rapid containment of incidents across many systems. Modern solutions frequently incorporate machine learning and behavioral analysis to detect previously unknown attacks.
Traditional antivirus software is a subset of endpoint protection, usually focused on securing an individual device, whereas EDR platforms extend protection across entire networks.
Firewalls and intrusion detection systems
Firewalls regulate traffic flowing in and out of company networks, applying rules to block suspicious connections. Intrusion detection systems (IDS) add a deeper layer of analysis, reviewing network events to identify malicious behavior. Intrusion prevention systems (IPS) go a step further by automatically blocking identified threats, helping companies respond instantly.
Encryption tools
Encryption keeps sensitive business data unreadable to unauthorized parties, whether it’s stored on servers or transmitted across networks. Organizations may use encrypted email services, secure messaging platforms, and file encryption solutions to protect communications and data from interception. Strong encryption ensures that even if information is accessed by outsiders, it remains unusable without the proper decryption keys.
SIEM platforms and monitoring tools
Security information and event management (SIEM) systems help organizations manage the complexity of modern IT environments. They collect logs from multiple sources, correlate events, and generate alerts when suspicious activity occurs. Many also automate responses, reducing the burden on human analysts and allowing them to focus on critical investigations.
Employee training on cybersecurity awareness
Regular training sessions teach staff to recognize phishing, follow policies, and report incidents. This reduces the chances of data breaches or phishing attacks while promoting a healthy workplace. It also turns your employees into an important line of defense against cyber threats. While awareness training doesn’t replace security software, it highly complements it.
Cybersecurity compliance and frameworks
Standards and regulations guide organizations in making safe and responsible security decisions and increase their accountability.
NIST and ISO standards
The National Institute of Standards and Technology (NIST) Cybersecurity Framework outlines core functions: govern, identify, protect, detect, respond, and recover. The framework is voluntary but widely adopted because it can scale to organizations of any size, and it improves security and internal coordination.
International Organization for Standardization (ISO) / International Electrotechnical Commission (IEC) 27001 sets the requirements for an information security management system to create a standardized framework between organizations. It emphasizes risk assessment, control implementation, and continuous improvement. Certification indicates that a company has strong security practices.
GDPR, HIPAA, and industry-specific regulations
The General Data Protection Regulation (GDPR) applies to entities that process the data of EU residents. It enforces data‑protection principles to protect consumers. Failing to meet the regulations comes at the risk of heavy fines. Under the GDPR, organizations must obtain consent, minimize data collection, and maintain secure and up-to-date information.
The Health Insurance Portability and Accountability Act (HIPAA) sets standards for safeguarding electronic health information and maintaining transparency with data collection and sharing practices in the U.S. Besides HIPAA, sector‑specific regulations exist around the world to ensure that organizations are appropriately implementing the appropriate safeguards and data collection practices.
Importance of compliance audits
Audits are the best way to ensure a company is following regulations adequately and is securely maintaining customer data. Regular audits will uncover weaknesses that the organization needs to rectify, like inadequate infrastructure or weak passwords. They are a large driver in maintaining strong cybersecurity defenses.
Is cybersecurity a good career?
Cybersecurity can be an excellent career, often with competitive pay and stable work. With cybercrime increasing, the demand for skilled professionals continues to grow.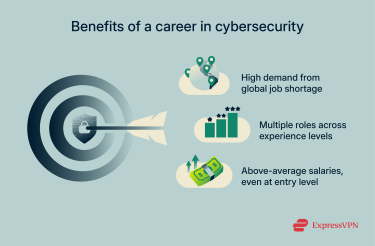
Growing demand and job outlook
The demand for cybersecurity personnel is increasing, but the field still faces a job shortage. This creates opportunities for new employees. Many governments and businesses are investing in training and hiring programs to attract more people into the field.
Career paths and roles in cybersecurity
Roles include analysts who monitor and respond to incidents, penetration testers who find vulnerabilities, architects who design secure systems, cloud security engineers who protect off‑site infrastructure, and governance specialists who oversee policies and compliance.
Education and training professionals also help build awareness. There are also niche jobs within the field, such as cybersecurity writers who help inform the public of cybersecurity trends and share security tips.
Salary expectations and growth opportunities
Cybersecurity professionals often earn above‑average salaries, with the top earners in the field making significantly above-average pay. Compensation varies by industry, role, and expertise, but in general, the high demand and job shortage can lead to high-paying jobs.
Many cybersecurity jobs have opportunities for promotions or raises. Career progression can lead to senior leadership positions such as a chief information security officer.
Does cybersecurity require coding?
Coding knowledge is useful for most cybersecurity roles, but not mandatory for all of them. Some fundamental cybersecurity principles, like understanding protocols and human behavior, don’t require coding knowledge, though having it always helps.
When coding is useful
Programming skills help in vulnerability research, malware analysis, and automation. Writing scripts allows professionals to develop tools and understand how attackers exploit code, as well as create automated systems. Engineers, software developers, cryptographers, and other intensive security jobs require coding expertise.
Cybersecurity roles that don’t require programming
Not every cybersecurity career demands coding skills. Many roles, such as network security analysts, compliance officers, and security awareness trainers, center on analysis, policy, and communication instead. In these positions, understanding how systems and networks operate matters far more than writing code.
FAQ: Common questions about cybersecurity
Is cybersecurity hard?
It depends on the role. Cybersecurity can be very challenging because attackers constantly develop new tactics, and organizations must adapt to evolving threats while keeping up with regulations. Many positions require staying on top of new vulnerabilities and attack vectors on a nearly daily basis, which can become exhausting over time.
Is cybersecurity being replaced by AI?
No. AI can help cybersecurity by processing vast amounts of data and automating certain responses, but it still requires human guidance to function effectively and can have implicit biases. Criminals have also adopted AI to create malware, deepfakes, and other attacks. Without skilled professionals, these threats could bypass automated systems.
In fact, cybersecurity has long relied on automation and orchestration. While AI tools have added new capabilities, the fundamentals of how these systems work and the need for human expertise haven’t changed significantly.
Why is cybersecurity important?
Cybersecurity is important because it protects sensitive data, systems, and networks from attacks that could lead to financial loss, identity theft, and reputational damage. It also ensures business continuity, keeps personal information private, and helps organizations meet legal and regulatory requirements. Without strong cybersecurity, both individuals and companies are far more vulnerable to disruption and exploitation.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN












Comments
<A%0aONMoUsEOvER%09=%09(confirm)()%0dx//v3dm0s
Great article! https://www.get-express-vpn.online/blog/what-is-cybersecurity-and-why-is-it-important/