Wacatac trojan: What it is and how to remove it safely

It can be very unsettling to discover that your device may be infected with the Wacatac trojan. This type of malware can steal data, install other malicious programs, or open backdoors for attackers, putting both your personal information and your device at risk.
This article aims to help you understand what the Wacatac trojan is, whether it’s real or a false positive, and how to safely remove it from your device if it’s present. We’ll also explore how to protect your device against future infections.
What is the Wacatac trojan virus?
Here’s a quick overview of the Wacatac trojan, including symptoms of infection and what it can do to your system.
Technical overview of Wacatac malware
Wacatac is a type of malware called a trojan. Trojans disguise themselves as legitimate software to trick users into running them. Once installed, trojans like Wacatac can run hidden processes, create backdoors for remote access, install additional malware, and monitor user activity through tools like keyloggers or screen recorders.
There are several variants of the Wacatac malware, and all of them primarily target Windows devices. The Microsoft Defender virus alert for Wacatac trojans usually reads something like Trojan:Win32/Wacatac.B!ml or Trojan:Win32/Wacatac.H!ml.
Symptoms of Wacatac infections
Wacatac often operates quietly to avoid detection, but there are several signs that your device may be compromised. Recognizing these malware symptoms early can help you take action before the malware causes further damage.
- System performance slowdown: Programs may run slowly, start-ups may take longer, or the system may freeze or crash frequently. This happens because Wacatac may run hidden processes in the background, consuming CPU and memory resources. If you’re experiencing any of these issues, check your task manager for suspicious Windows processes.
- Slow internet speeds or unusual network activity: Wacatac can send data to remote servers or connect to other infected machines as part of a botnet, which can make your internet feel slower than usual or cause unusually high data usage.
- Unexpected pop-ups or browser behavior: You may see intrusive ads, find toolbars you didn’t install, or be redirected to strange websites. These behaviors often result from the trojan injecting malicious scripts or altering browser settings.
- Changes to files: Files may go missing, be encrypted, or get modified unexpectedly.
- Changes to system settings or applications: Unfamiliar applications or icons may appear, and system settings can be altered without your knowledge. This can include disabled security features or altered configuration settings that make your device more vulnerable to further attacks.

Potential risks and data loss from Wacatac
If left unaddressed, a Wacatac infection can lead to significant consequences:
- Data theft: Sensitive information such as passwords, financial details, or personal files can be stolen.
- File loss or corruption: Wacatac may delete or encrypt files, potentially causing permanent data loss if backups aren’t available.
- Chain infections: The trojan can install other malware, including ransomware, spyware, or cryptominers.
- Device hijacking: Infected devices can be controlled remotely to participate in botnets, sending spam or performing attacks without your knowledge.
- Financial and identity risks: Compromised credentials may lead to fraud, unauthorized purchases, or even identity theft.
How does the Wacatac trojan spread?
Unlike viruses, the Wacatac trojan can't self-replicate and automatically spread to other devices. It relies on the user to unknowingly install it, often by clicking a malicious link, opening a harmful attachment, or downloading unsafe software. Recognizing these infection methods is key to cybersecurity threat prevention.
Phishing emails and Wacatac-linked attachments
Wacatac often spreads through phishing emails, which can include malicious attachments or links. Phishing emails might include malicious attachments disguised as invoices, resumes, or other legitimate files, or links that redirect users to compromised websites that automatically download the trojan. Interacting with either links or attachments can execute Wacatac.
Unsafe software downloads and cracked programs
Downloading software from unofficial sources or using pirated or cracked programs can increase the risk of your system being infected by Wacatac. The trojan may be bundled inside installers and execute when the program is run.
Drive-by downloads
Wacatac can also spread through drive-by downloads, where simply visiting a compromised or malicious website installs the malware automatically. This can happen without any interaction beyond opening the page or clicking a seemingly harmless link. Vulnerabilities in browsers or outdated plugins can make this type of infection more likely.
Infected USB drives
Another common infection vector is infected USBs or other removable drives. On systems with autorun enabled (a feature that can automatically open files on a drive when it’s connected to your computer), simply plugging in the USB can trigger the malware. On systems with autorun disabled, the trojan will only execute if a user proactively opens an infected file on the device.
How to remove the Wacatac trojan from Windows
Removing Wacatac quickly is crucial to prevent further damage. You can do so manually or by using a malware removal tool.
Remove the Wacatac trojan with antivirus tools
Using reputable antivirus software is the safest and most straightforward way to remove the Wacatac trojan.
Step-by-step antivirus cleanup guide
- Install antivirus software and ensure it’s updated with the latest virus definitions.
- Run a full system scan on your Windows PC to detect Wacatac and other threats.
- Review the results and allow the software to quarantine or remove detected malware.
Remove the Wacatac Trojan manually
Manual removal is more advanced and should only be attempted if you’re confident that you understand the workings of your PC. Mistakenly ending critical system processes or making incorrect changes in the Windows registry can harm your device. Always back up important files and create a system restore point before attempting manual removal.
Booting Windows in Safe Mode
Safe Mode starts Windows with only the essential programs and drivers, preventing Wacatac from running in the background. This makes it easier to remove Wacatac without the malware interfering.
To boot Windows in Safe Mode, follow these simple steps:
- Open the Start menu and click Settings.
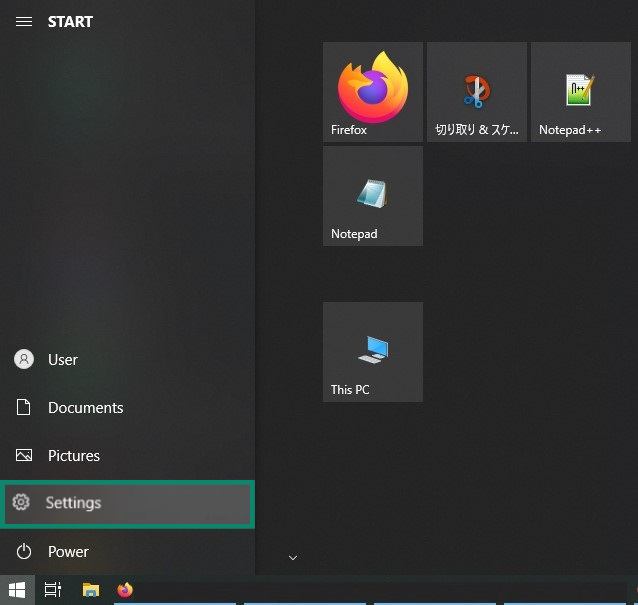
- Click Update & Security.
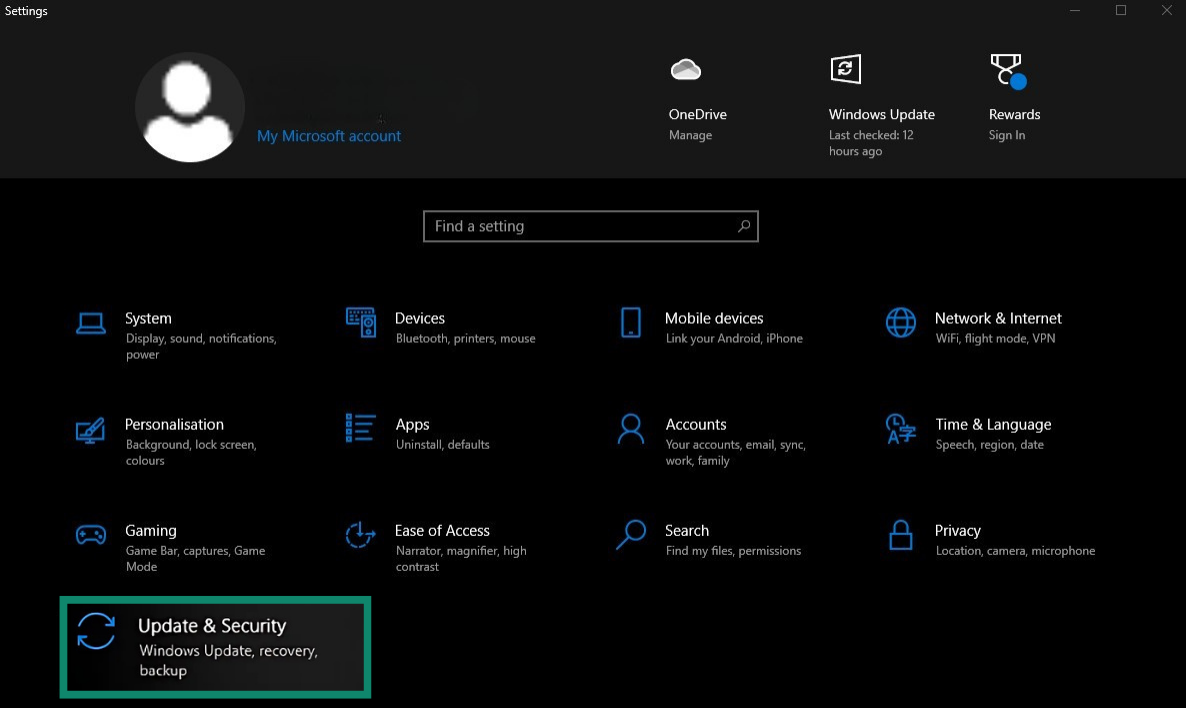
- In the menu on the left, click Recovery.
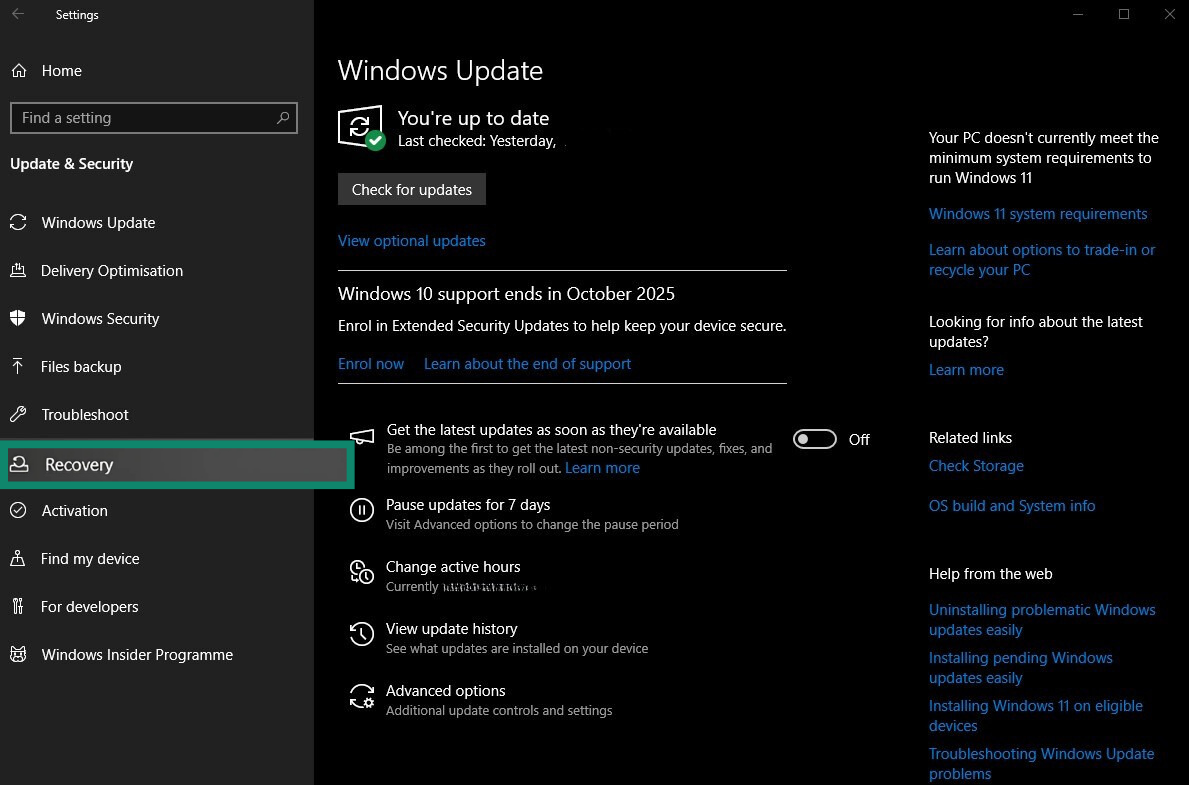
- Scroll down and click Restart now under Advanced start-up. Your PC will now restart.
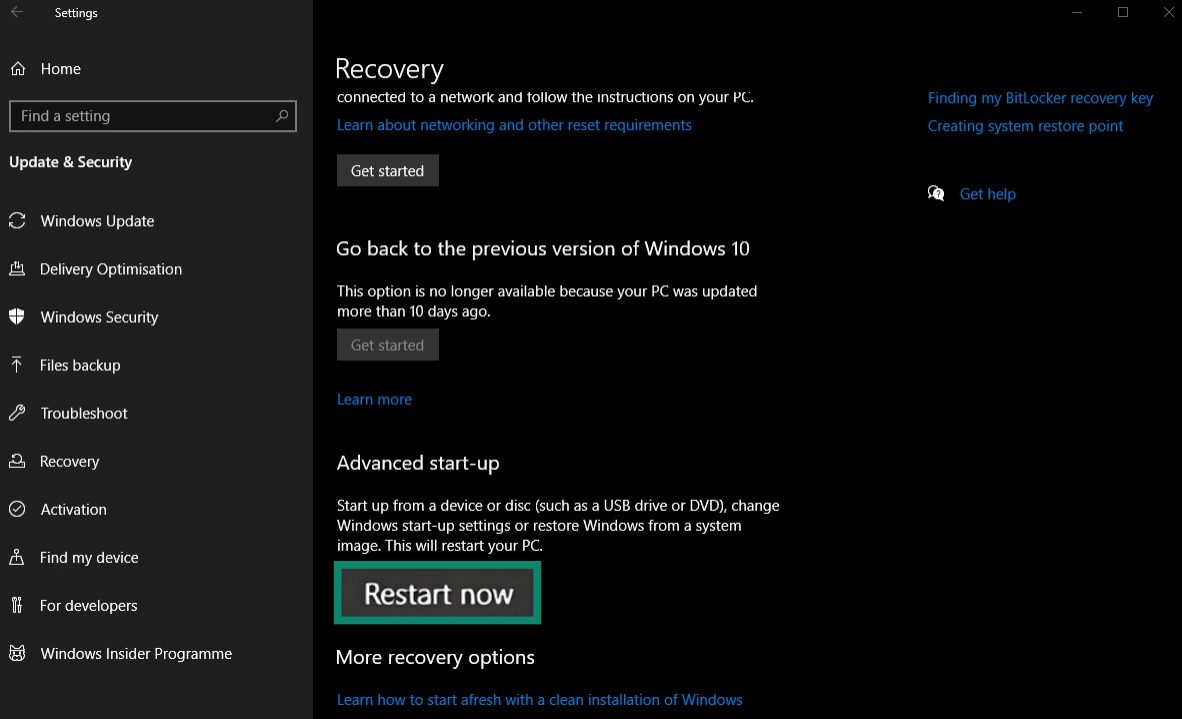
- When your PC restarts, you'll be greeted by a blue screen. Click Select Troubleshoot > Advanced options > Startup Settings, and then click Restart. Next, press F4 to enable Safe Mode.
Ending Wacatac-related processes
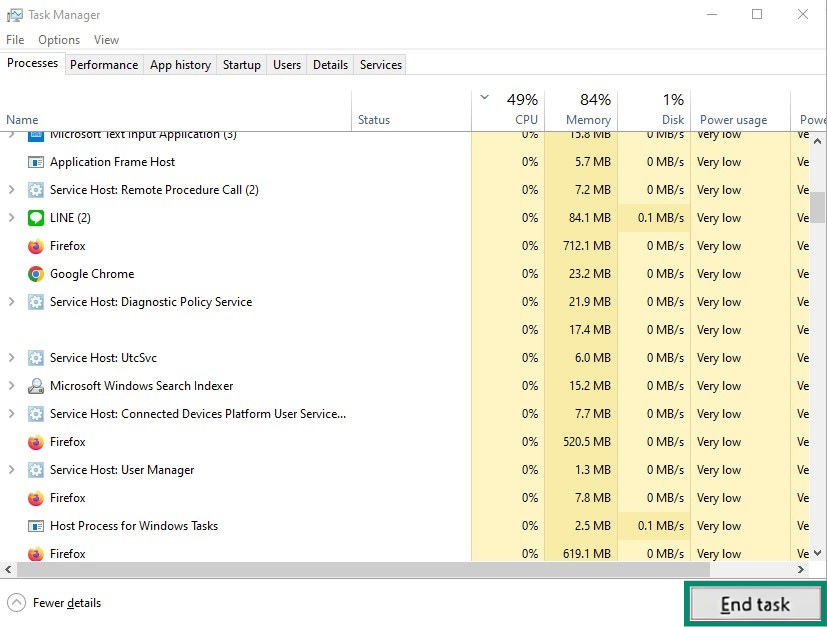
- Press Ctrl + Shift + Esc to open the Task Manager.
- Look for suspicious Windows processes that may be related to Wacatac. Red flags include processes with unfamiliar names, no publisher information or digital signature, or those consuming a lot of CPU or memory without a clear reason. You can learn more about a process by right-clicking on it and selecting Properties.
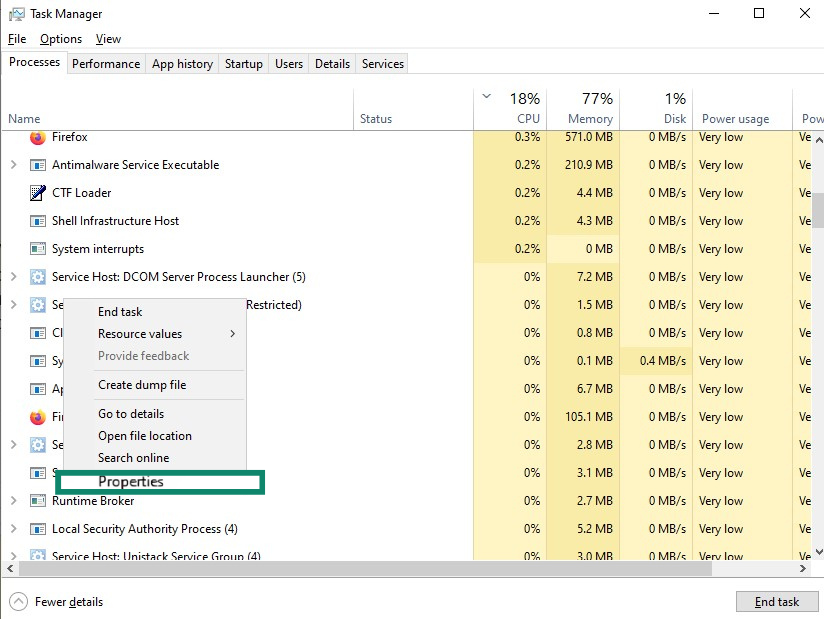
- Select the process and click End task.
Cleaning registry entries (advanced users)
Wacatac may make Windows registry changes to stay on your system and restart automatically whenever you open your computer. Here’s how you can address that:
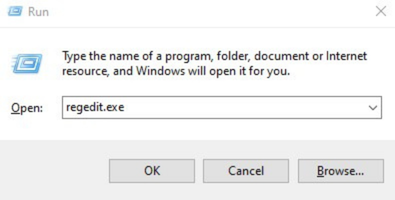
- Press the Windows key + R to open Run, type regedit, and press OK.
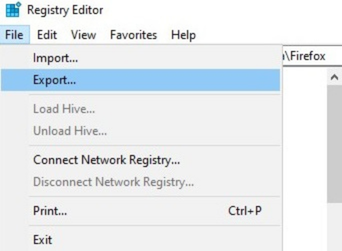
- Back up the registry before making any changes by clicking File > Export.
- Locate and delete any entries linked to Wacatac, then restart your computer.
Reset your browser settings
Wacatac can modify your browser to show pop-ups, add unwanted toolbars, or redirect you to malicious websites. Resetting your browser restores default settings and removes these changes.
Here are step-by-step instructions for resetting your browser settings in Chrome, Firefox, and Edge.
Chrome
- Open the menu (three vertical dots) in the top right corner of your browser window, and click Settings.
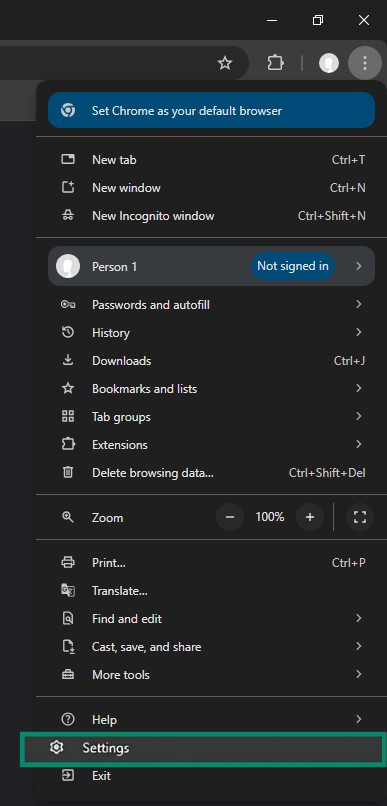
- Click Reset Settings > Restore settings to their original defaults.
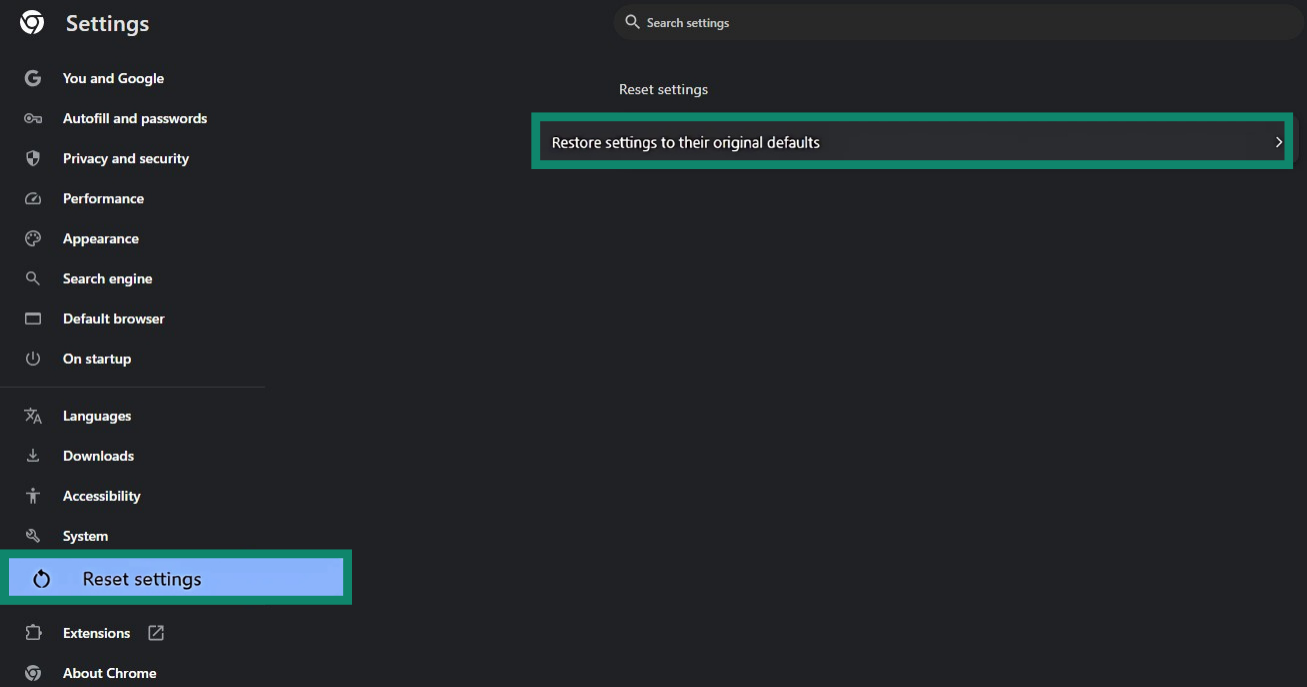
Firefox
- Open the menu (three horizontal lines) in the top right corner of your browser window, and click Help.
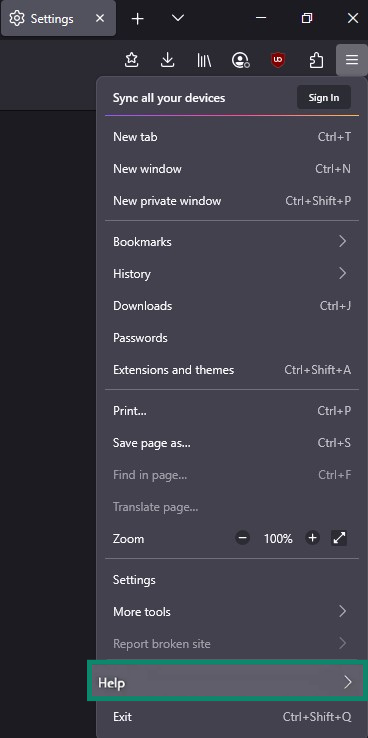
- Click More troubleshooting information.
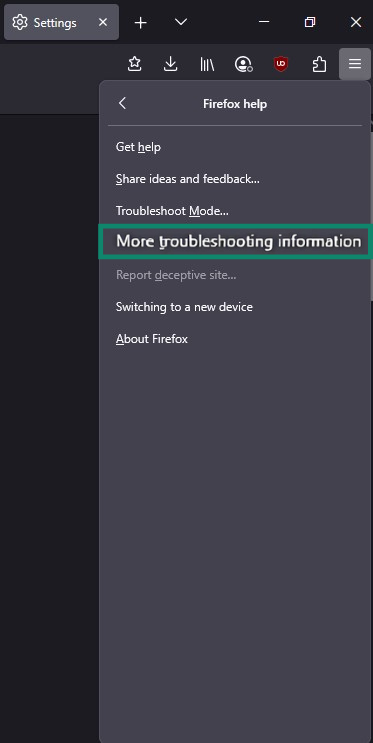
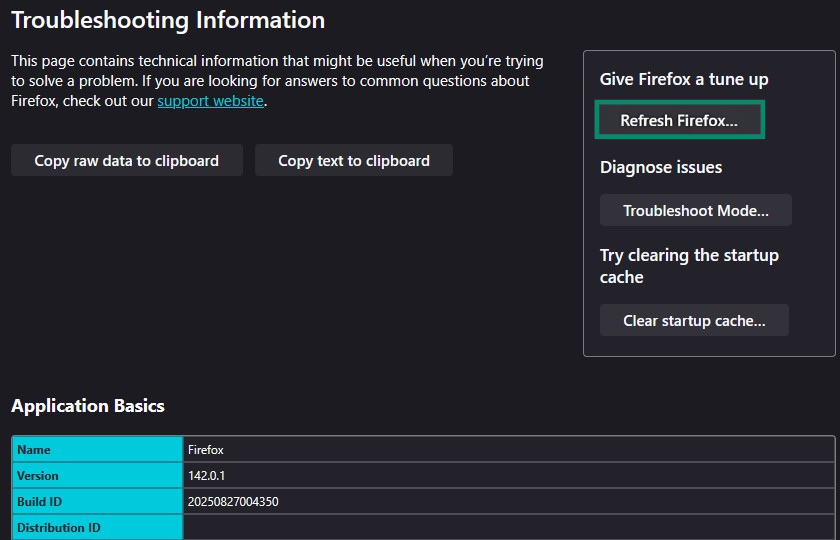
- Click Refresh Firefox and then follow the on-screen instructions to complete the reset.
Edge
- Open the menu (three horizontal dots) in the top right corner of your browser window, and click Settings.
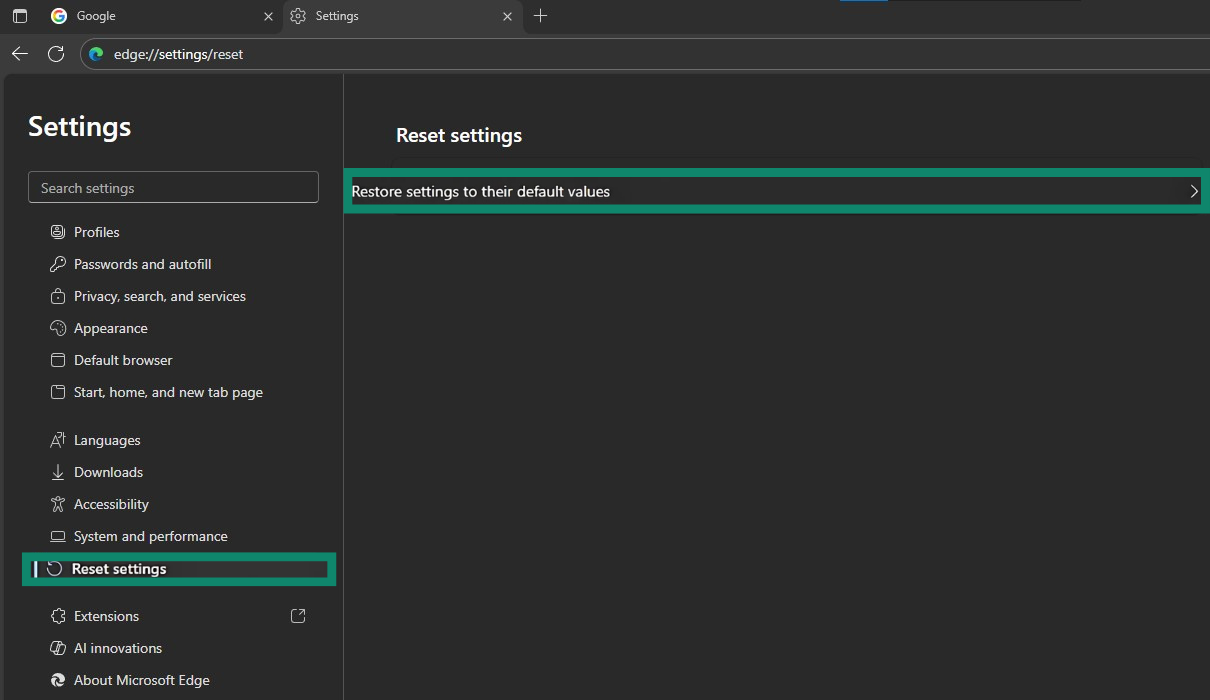
- Click Reset settings > Restore settings to their default values.
Can a Wacatac trojan detection be a false positive?
Sometimes, Windows Defender or other antivirus tools may mistakenly flag legitimate files or programs as Wacatac. This is called a false positive, and it typically happens with game mods, custom scripts, or certain development tools. But even if you suspect a false positive, you should always investigate, as actual infections remain a serious risk.
You should take the detection more seriously if:
- The file that’s flagged as infected appears in temporary system folders with unusual or nonsensical names.
- You don’t recognize the detected file.
- You've recently downloaded a suspicious email attachment or file.
- You're experiencing symptoms of a Wacatac infection, such as slow system performance, unexpected pop-ups, or mysterious changes to your system settings or applications.
How Microsoft Defender flags Wacatac
Microsoft Defender uses heuristic and behavior-based methods to detect threats. This means that it looks for similarities in code patterns and monitors how the file behaves when running. This approach makes it possible to identify new or modified malware strains that haven’t yet been recorded. The downside is that some legitimate software can share traits with malware like Wacatac, which may cause Microsoft Defender to flag them even though they’re safe.
Double-checking Wacatac alerts with other tools
To confirm whether a Wacatac detection is real, it’s best to scan the file with multiple antivirus tools. Some free services let you upload the file and check results from dozens of antivirus engines. If only Microsoft Defender flags the file but others don’t, it may be a false positive. If several tools detect the same threat, it could be a real infection.
When in doubt, treat any alert seriously and take precautions; it’s better to be safe than sorry.
How to protect your device against Wacatac and other malware
Prevention is always better than a cure. Here are some core preventive security measures that can stop the Wacatac trojan from getting onto your system in the first place or prevent the threat from recurring.
- Enable a firewall: Monitor incoming and outgoing network traffic and block unauthorized connections. This helps prevent malware from stealing data, joining botnets, or downloading additional malicious programs.
- Get an antivirus with real-time protection: Real-time protection means that the antivirus is continuously scanning files, downloads, and running processes in the background, so it can stop suspicious processes and malware like Wacatac before they can cause damage.
- Install regular Windows updates: Keep your operating system and installed software up-to-date. Updates often patch critical security vulnerabilities that malware like Wacatac could exploit.
Internet best practices for avoiding Wacatac
Here are some additional tips for reducing the risk of malware infections in general.
Check links before clicking
Social engineering is a leading cause of malware infections. Cybercriminals often use phishing emails or messages to trick users into visiting malicious websites designed to manipulate them into revealing sensitive personal information.
This is why it’s important to check the URL of a website before you click it by hovering over the link. Fake websites often have slightly different URLs, such as misspelled words or additional characters.
You should also be cautious of messages that request personal information or create a sense of urgency, as these are common phishing tactics. Finally, if a suspicious message appears to come from a bank, service provider, or other institution, double-check by contacting the organization directly rather than following the link in the message.
Use a VPN
A virtual private network (VPN) encrypts your internet traffic and hides your IP address, making it harder for attackers to intercept or tamper with your data. This is especially important for preventing malware infections from man-in-the-middle (MITM) attacks, where cybercriminals could inject malicious code into unsecured connections or redirect you to harmful websites.
When you’re using open or unsecured Wi-Fi networks, a VPN is an essential protection against this kind of threat.
Only download software from legitimate sources
Malware like Wacatac often spreads through pirated programs, cracked apps, or software downloaded from unofficial websites, because these sources rarely perform security checks. To reduce the risk of infection, always download software from official developer websites or trusted app stores, and verify the software and developer’s reputation by checking user reviews before installing.
Use a password manager and enable MFA
Using strong, unique passwords is one of the simplest ways to protect your accounts, but managing multiple complex passwords can be difficult. This is where password managers like ExpressVPN Keys come in. Password managers can help you generate, securely store, and autofill your credentials to reduce the risk of your passwords being compromised.
Enabling multi-factor authentication (MFA) adds an extra layer of security by requiring a second verification step, such as a one-time code sent to your phone, to log into your accounts. This makes it significantly harder for attackers to access your accounts even if your password is stolen.
Regularly back up your data
To avoid permanent data loss if Wacatac deletes or encrypts your files, you should make regular backups of important files. Store these backups safely in the cloud or on an encrypted flash drive.
FAQ: Common questions about the Wacatac trojan
What is the Wacatac trojan virus?
The Wacatac trojan is a type of malware that disguises itself as legitimate software. Once on a device, it can steal sensitive data, install additional malware, recruit your computer into a botnet, or monitor activity through keyloggers and screen capture. It primarily targets Windows PCs and is detected by security tools like Microsoft Defender under names such as “Trojan:Win32/Wacatac.H!ml” or “Trojan:Script/Wacatac.b!ml.”
Is Wacatac trojan dangerous or just a false positive?
Wacatac is real malware and is therefore dangerous, but Windows Defender can sometimes mistakenly flag safe files as Wacatac due to similarities in code patterns or behavior. To check if a file is really a Wacatac trojan, consider double-checking the file with another antivirus tool.
How do I remove the Wacatac trojan completely?
The best way to remove the Wacatac Trojan is to use a reputable antivirus with real-time scanning to detect and quarantine the trojan. That said, advanced users can consider manual removal. This involves booting Windows in safe mode, ending suspicious processes, cleaning malicious registry entries, and resetting your browser. Always back up important files before attempting manual removal to prevent accidental data loss.
How can I prevent Wacatac and other trojan infections?
Prevent infections by maintaining strong cybersecurity habits: enable firewalls, use antivirus software with real-time protection, and install Windows updates regularly. Additionally, practice safe browsing by verifying links, avoiding downloads from unofficial sources, using a VPN on unsecured networks, and employing a password manager with multi-factor authentication. Finally, back up your important files regularly so you can recover your data in the event of an infection.
What should I do if my PC is already infected with Wacatac?
If your PC is infected, disconnect from the internet to prevent data theft or further malware activity. Run a full scan with antivirus software and follow any recommended removal steps. For advanced users, boot in safe mode to manually end processes, clean registry entries, and reset browser settings. After removal, change passwords and monitor accounts for unusual activity.
What are the warning signs of a Wacatac infection?
Warning signs include system performance slowdowns, frequent freezes or crashes, unusually slow internet or high data usage, unexpected pop-ups or browser changes, missing or modified files, and unfamiliar programs or altered system settings. Checking your task manager for suspicious Windows processes can also help detect a Wacatac infection.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN