Symmetric vs. asymmetric encryption: What’s the difference and why it matters
Encryption isn’t just one thing; it comes in different forms, and two of the most important are symmetric and asymmetric encryption. Both play a huge role in keeping data safe, but they do it in very different ways. Understanding how they compare helps make sense of everything from secure messaging apps to online banking.
This guide will break down the key differences between the two methods, show you where each one is used, and explain why it matters for your security.
What is encryption, and why do we need different types?
Encryption turns readable data (plaintext) into unreadable data (ciphertext), so only someone with the right key can unlock it. It’s built into your phone, browser, and apps to keep logins, messages, and files private. Without it, anyone on the same network, from cybercriminals to Wi-Fi owners to internet service providers (ISPs), could intercept or tamper with your data.
But not all encryption works the same way. Some methods are designed for speed and efficiency, others for secure key exchange or digital signatures. No single approach can balance security, performance, and scalability in every situation. That’s why modern systems use different types of encryption (often in combination) depending on the job.
A brief history of encryption systems
People have been hiding messages for as long as they’ve had secrets. Ancient civilizations used simple hand ciphers, while the 20th century brought the famous Enigma machines. In the 1970s, public-key cryptography (PKC) revolutionized the field by allowing strangers to build trust without ever meeting. A generation later, Advanced Encryption Standard (AES) became the go-to standard for fast and reliable data protection. The tools keep changing, but the mission stays the same: keeping secrets safe.
Learn more: For the complete timeline, take a look at our detailed guide to encryption history.
What makes encryption secure?
Secure encryption rests on the following pillars:
- Key length: Longer cryptographic keys generally provide stronger security by creating more possible combinations for attackers to try.
- Algorithm complexity: More sophisticated mathematical operations make it harder for attackers to find patterns or weaknesses.
- Key secrecy: The encryption is only as strong as the protection of the keys themselves.
- Implementation quality: Even strong algorithms can be compromised by poor coding or configuration.
In short, encryption is secure when the only practical way to get your data is to guess the secret key. And that guess would take an absurd amount of time with nowadays computers.
What is symmetric encryption?
Symmetric encryption (also known as symmetric key encryption, symmetric key cryptography, or secret-key encryption) is a way of securing data using a single shared key for both locking (encryption) and unlocking (decryption). Its strength lies in being simple and efficient, which makes it ideal for protecting everything from files on your device to the data your apps send and receive every second.
How symmetric encryption works
With symmetric encryption, both sides share one secret key. You generate a strong random key, encrypt data with it, send the ciphertext, and the recipient decrypts with the same key. This straightforward mathematical operation makes symmetric encryption generally faster than asymmetric encryption, as it needs less computational power.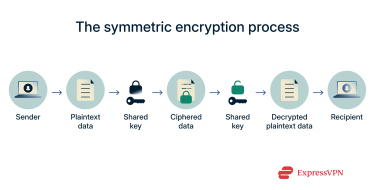
Examples of symmetric encryption algorithms
Several symmetric encryption algorithms are widely used today. An encryption algorithm is essentially a set of mathematical rules that determine how data is scrambled with a key and then unscrambled by someone who has the right key. The goal is always to keep information private, but each algorithm is designed differently to balance speed, efficiency, and security for specific needs:
- AES: AES is the global standard for encryption. It’s a block cipher, which means it secures data by locking it in fixed-size chunks. It comes in different key strengths (128-bit AES, 192-bit AES, and 256-bit AES), with larger numbers offering greater security. You will find AES protecting files on your computer, securing financial transactions in banking apps, and forming the backbone of virtual private networks (VPNs) and secure websites.
- ChaCha20-Poly1305: ChaCha20 is a stream cipher, so it encrypts data in a continuous flow rather than in separate blocks. This design makes it very fast and efficient, especially on mobile devices. It is almost always combined with Poly1305 to provide Authenticated Encryption with Associated Data (AEAD). This is a powerful two-in-one feature: it both encrypts your data for secrecy and generates a tag to confirm that no one has tampered with it.
- XChaCha20-Poly1305: This is a modified version of ChaCha20 built for situations with massive amounts of data. It uses a longer nonce, a unique “number used once” that prevents attackers from capturing and replaying old messages. The extended nonce provides an extra layer of safety, making it a strong choice for systems that encrypt many messages with a single key.
- Other notable ciphers: You might also encounter algorithms like Camellia, a strong block cipher similar to AES, or Twofish and Serpent, which were finalists in the competition that AES won. While highly secure, they are less common in everyday applications.
Advantages and disadvantages of symmetric encryption
Symmetric encryption offers exceptional performance for protecting large amounts of data, but this speed is balanced by the central challenge of securely managing and sharing its single secret key.
| Advantages | Disadvantages |
| Speed and efficiency: Designed for encrypting large volumes of data quickly with minimal processing power. | Key distribution problem: Securely sharing the secret is hard; interception exposes encrypted data. |
| Low computational overhead: It’s light on CPU and RAM, making it suitable for embedded systems and mobile devices. | Key management complexity: As users grow, the number of required shared keys scales exponentially, n(n−1)/2 per the National Institute of Standards and Technology (NIST), making administration difficult in large networks. |
| Strong security: When used with modern ciphers (like 256-bit AES) and proper implementation, it resists all current practical attacks. | Scalability issues: The need for pairwise shared secrets means it doesn’t scale well across large, dynamic networks. |
| Simplicity: One key for encryption/decryption, and straightforward to implement. | No built-in authentication: The key itself doesn’t verify the sender’s identity, requiring extra mechanisms, like message authentication codes (MACs), to prevent tampering. |
| Single point of failure: If the shared key is ever compromised, all past and future communications using that key are at risk. |
What is asymmetric encryption?
Asymmetric encryption, also known as asymmetric key encryption or public key cryptography (PKC), is a way to protect your information using two different but mathematically linked keys: a public key and a private key.
This two-key system solves a major problem in cybersecurity: how to share a secret message with someone without having to secretly share a key with them first.
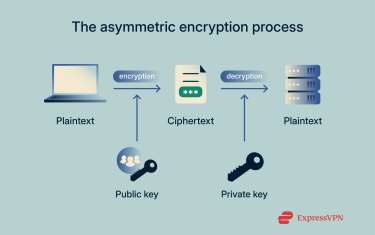
How asymmetric encryption works
If you have ever wondered how public key encryption works, the process is simple and secure.
- Get the public key: If you want to send a secure message to a friend, you first get their public key.
- Encrypt the message: You use a public key to “lock” your message. Once it’s locked, it can only be unlocked by the matching private key.
- Send it securely: You can now send this encrypted message over any network. Even if it’s intercepted, it’s unreadable.
- Decrypt the message: Your friend receives the message and uses their private key to unlock and read it.
PKC isn’t just for keeping messages secret; it’s also the basis for digital signatures. Instead of encrypting data, your private key is used to generate a unique signature for the message. Anyone with your public key can then verify that the signature really came from you and that the message hasn’t been changed.
Examples of asymmetric encryption algorithms
Asymmetric algorithms solve different security problems, from exchanging secrets to verifying identity. Most are based on difficult mathematical challenges that are simple to create but extremely hard to reverse without the private key.
- Rivest-Shamir-Adleman (RSA): RSA is the original public-key algorithm and for decades was the backbone of internet security. Its strength comes from the difficulty of factoring large prime numbers. While still in use, modern systems often prefer more efficient alternatives.
- Elliptic curve cryptography (ECC): ECC is the modern workhorse of PKC. It provides the same level of security as RSA but with much smaller and faster keys. This efficiency makes it the standard choice for securing everything from secure messaging apps and cryptocurrencies to the connections your smartphone makes every minute.
- Diffie-Hellman key exchange (DH): This is not an encryption algorithm itself but a clever method for two parties to securely agree on a shared secret key over an insecure network. It’s the “digital handshake” that happens in the background when your browser connects to a secure website or your VPN establishes a tunnel. This process generates the temporary symmetric key needed for the rest of the session.
- Digital Signature Algorithm (DSA): As its name suggests, this algorithm is used exclusively for creating digital signatures. A digital signature proves that a message or file came from a specific sender and has not been altered. It is a key tool for verifying software updates and authenticating official documents.
- Post-quantum cryptography (PQC): This is the next generation of public-key algorithms. Today’s mainstream methods, like RSA and ECC, are vulnerable to attacks from future quantum computers. PQC algorithms are being designed and standardized now to ensure our data remains secure against that future threat.
Advantages and disadvantages of asymmetric encryption
Asymmetric encryption’s main advantage is its ability to create trust and exchange secrets over public networks; this strength is balanced by slower performance and higher computational demands. Let’s look at the pros and cons in more detail:
| Advantages | Disadvantages |
| Secure key exchange: You can freely share your public key over an insecure network without compromising your private key, allowing anyone to send you an encrypted message that only you can open. | Performance: The mathematical operations behind asymmetric encryption are very complex. This makes it slower than symmetric encryption and impractical for encrypting large volumes of data. |
| Authentication and non-repudiation: By signing a message with your private key, you prove your identity. Anyone can then use your public key to verify that the message is authentic and came from you. | Computational intensity: The slow performance means it requires much more processing power (CPU) and energy, which can be a problem for low-power devices like smartphones or IoT sensors. |
| Versatility: It can be used for a number of applications, such as email, online banking, and e-commerce, and to secure Secure Sockets Layer (SSL) / Transport Layer Security (TLS) connections typically used when securing internet traffic. | Larger key sizes: To achieve the same level of security as symmetric encryption, asymmetric keys must be much longer. For example, a 2048-bit RSA key is considered equivalent to only a 128-bit symmetric key. |
| Non-Repudiation: Because a signature is created with a unique private key, the sender cannot later deny having sent the message. This is critical for legal and financial transactions. | Quantum exposure: The most common asymmetric algorithms, like RSA and ECC, are vulnerable to attacks from future quantum computers, which could solve the underlying mathematical problems relatively easily. |
Symmetric vs. asymmetric encryption: Key differences
The key differences between symmetric and asymmetric encryption aren’t about which one is stronger but about how each method balances the trade-offs between speed, key management, and the ability to establish trust.
Speed and performance
For moving data at scale, symmetric encryption is the engine you rely on: it processes streams and large files with low latency and minimal battery drain. Asymmetric cryptography carries a different load. It handles the small but important jobs like handshakes, key agreement, and digital signatures, so you use it sparingly to set up trust and then hand off to symmetric ciphers for the heavy lifting.
Key management and distribution
Symmetric systems demand a safe way to share secrets and a plan to rotate them, which gets messy as participants multiply. Asymmetric systems avoid that bottleneck by letting you publish public keys openly while locking down private keys, so each person or service keeps a single key pair that scales across many counterparties without an explosion of shared secrets.
Use cases and real-world applications
Different scenarios call for different encryption approaches based on their specific requirements:
Scenarios where symmetric encryption is better
Choose symmetric encryption when speed and efficiency matter most:
- It’s the right fit for large data volumes like databases, file systems, and streaming media.
- It suits resource-constrained contexts such as Internet of Things (IoT), embedded devices, and mobile apps because it uses little CPU and memory.
- It powers high-performance workloads like real-time, secure communications, video streaming, and online gaming.
- It’s the standard for data at rest across files, databases, and backups, and after an initial handshake, VPN tunnels switch to symmetric keys to keep throughput high.
When asymmetric encryption is the right choice
Reach for asymmetric cryptography whenever security and identity verification are the top priorities. You rely on it every day for:
- Digital signatures: Verifying that a software update or a document is from a legitimate source and hasn't been altered.
- Secure messaging apps: Protecting your private conversations with end-to-end encryption (E2EE).
- Cryptocurrencies: Securing your digital wallet and authorizing transactions on the blockchain.
- Secure web browsing (SSL/TLS): It’s the system that manages the digital certificates behind the padlock icon in your browser, proving a website is authentic and protecting your connection to it.
Which encryption is more secure?
Neither wins by default; both are extremely strong when modern algorithms, solid randomness, correct modes, and careful key handling are in place. Real risk usually comes from everything around the math: weak keys, leaky implementations, bad protocol choices, or poor storage. So, the right answer is to pair asymmetric for setup and signatures with symmetric for data and execute both cleanly.
Side-by-side comparison table
| Symmetric | Asymmetric | |
| Keys | One shared secret key used for both encryption and decryption | Two keys: a public one (shared) and a private one (kept secret) |
| Key exchange | Tricky: you must send the secret safely somehow | Built-in: just share your public key |
| Speed | Very fast, good for big data | Slower, good for setup and small tasks |
| Scale | Gets messy: need a unique key with every person | Simple: each person only needs one key pair |
| Identity | Doesn’t prove who you are unless you add something extra | Can prove identity with digital signatures |
| Common uses | Encrypting files, disks, VPN data, website traffic once set up | Handshakes, digital signatures, exchanging keys |
| Examples | AES, ChaCha20 | RSA, ECC |
The hybrid approach: Best of both worlds
Modern protocols combine both on purpose. Asymmetric cryptography lets strangers prove identity and agree on fresh secrets without sharing a password. Symmetric ciphers then carry the data at speed with low latency and battery cost. This is the model behind E2EE in secure messaging apps: devices perform a public-key handshake to securely exchange keys, then protect the actual conversation with fast symmetric ciphers.
ExpressVPN’s Lightway protocol follows this same pattern: a public-key handshake sets short-lived keys, a fast AEAD cipher protects the tunnel, and periodic re-keys preserve forward secrecy.
That’s why the right answer isn’t “pick one”; it’s “use both, in order.” Authenticate and agree on secrets with asymmetric cryptography, encrypt the payloads with symmetric cryptography, and rotate keys so any single leak has a small blast radius. When you evaluate tools, look for this pattern. When you design systems, bake it in from the start.
How encryption supports data privacy and VPNs
A VPN establishes a secure tunnel between your device and the internet to ensure data transfer. When you use a VPN, all your traffic is sent through this tunnel. Your data is first encrypted into unreadable code before it leaves your device. Your ISP can see you are connected to a server, but it cannot read the data passing through the tunnel, such as the websites you visit or the files you download. Once your encrypted traffic reaches the VPN server, it is decrypted and then sent to its final destination on the internet. This action shields your personal IP address and approximate location, as the website sees the request coming from the server, not from you. This process happens in reverse for incoming data, protecting it all the way back to your device. This back-and-forth keeps your information unreadable and private from any third parties who might try to intercept it.
Once your encrypted traffic reaches the VPN server, it is decrypted and then sent to its final destination on the internet. This action shields your personal IP address and approximate location, as the website sees the request coming from the server, not from you. This process happens in reverse for incoming data, protecting it all the way back to your device. This back-and-forth keeps your information unreadable and private from any third parties who might try to intercept it.
VPNs typically use encrypted communication protocols like WireGuard or OpenVPN, which implement both symmetric and asymmetric encryption. Some providers develop their own protocols; for instance, ExpressVPN’s Lightway protocol is designed for speed and reliability, performing well even when you switch between different networks, like moving from a Wi-Fi connection to your mobile data.
Why do both encryption types matter? The app authenticates the server and agrees on fresh session secrets using asymmetric cryptography, then protects all traffic with fast symmetric ciphers (AEAD), such as ChaCha20-Poly1305, which both encrypt data and verify it hasn't been tampered with.
ExpressVPN’s Lightway follows this hybrid pattern. It re-keys to preserve forward secrecy, a feature that means if a single key is ever compromised, it can’t be used to decrypt past communications as you move between networks.
FAQ: Common questions about symmetric and asymmetric encryption
What is the difference between asymmetric and symmetric encryption?
The difference is straightforward. Symmetric uses one shared secret. It’s fast and efficient, but you must share that key safely. Asymmetric uses a public key and a private key. It’s slower, but it enables identity and secure key exchange. Use asymmetric for handshakes and signatures; use symmetric for bulk data once trust exists.
Is AES encryption symmetric or asymmetric?
Advanced Encryption Standard (AES) is symmetric. The same secret key encrypts and decrypts, which is why it protects files, databases, backups, and the data phase of HTTPS and VPN tunnels. It supports 128/192/256-bit keys, and 256-bit AES gives wider margins. Because both sides need the same key, systems pair AES with an asymmetric handshake to agree on a fresh session key.
What is an example of asymmetric encryption?
Rivest–Shamir–Adleman (RSA) and elliptic curve cryptography (ECC) anchor HTTPS handshakes: your browser uses the site’s public key to protect a one-time session secret that only the private key can recover. The same model underpins Pretty Good Privacy (PGP) / Secure/Multipurpose Internet Mail Extensions (S/MIME) email, Secure Shell (SSH), code signing, and cryptocurrency wallets. Asymmetric sets trust; symmetric takes over for the heavy data.
When to use symmetric vs. asymmetric encryption?
Use symmetric for speed: large transfers, storage, streaming, and record layers after a handshake; it also suits constrained devices. Use asymmetric when meeting new parties, proving identity, or exchanging keys across untrusted networks. Most systems do both: asymmetric bootstraps trust, and symmetric protects the session.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN