Space cybersecurity: What it is and why it matters

A morning like any other. You tap your phone for a rideshare and check the forecast before going out. These actions rely on satellites that orbit hundreds or even thousands of kilometers above you.
If attackers cut those links, payments fail, cars lose navigation, and emergency crews scramble for backup channels. Satellite services were once peripheral to everyday connectivity, but today, they’re deeply woven into critical infrastructure. That shift puts space assets squarely in the crosshairs of criminals, hacktivists, and state-sponsored teams.
This guide explores what makes cybersecurity in space different from traditional security approaches, why it matters for everyday life, and how organizations can protect these critical systems.
What is space cybersecurity?
Unlike “normal” cybersecurity, space cybersecurity focuses on the protection of space-based systems and networks from cyber threats. It’s about extending the principles of information security (confidentiality, integrity, and availability) to one of the most advanced frontiers of technology.
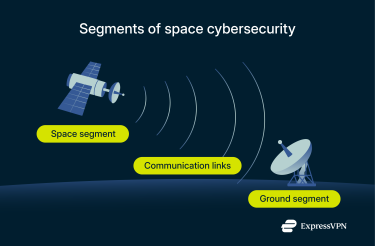
It blends traditional IT security, network security, and even industrial control system security (for satellite operations) with the specialized aspects of space operations, securing:
- Space segment: Satellites, on-board computers, attitude-control units, and software-defined radios.
- Ground segment: Antennas, fiber backhaul, data centers, and DevOps pipelines that push code to orbit.
- Links between them: Radio frequency uplinks/downlinks, laser cross-links, and leased terrestrial networks.
In practical terms, space cybersecurity involves measures like encryption of communications (both uplink commands and downlink data), strong authentication for satellite control access, on-board intrusion detection systems, and security in the ground segment (e.g., securing mission control networks and cloud systems that manage satellite data).
It also means preparing for incidents with resilience, making sure that a satellite or network can continue operating, even in a degraded mode, under attack or can be recovered quickly after a breach.
Why space needs cybersecurity now more than ever
Space systems have transitioned from niche utilities to essential infrastructure virtually overnight. Given how interconnected space systems are with other critical infrastructure like communications, power grids, transportation, etc., maintaining the cybersecurity of space assets is now recognized as vital for national security and the global economy.
The rise of satellite infrastructure
The number of satellites in orbit is climbing at a staggering rate. In 2018, a single Falcon 9 rocket (a reusable launch vehicle developed by SpaceX) carried 64 cubesats into space. These are small, standardized satellites roughly the size of a shoebox, used for a variety of scientific and commercial purposes. By mid-2023, there were over 9,115 active satellites orbiting Earth, a 35% jump since just January 2022.
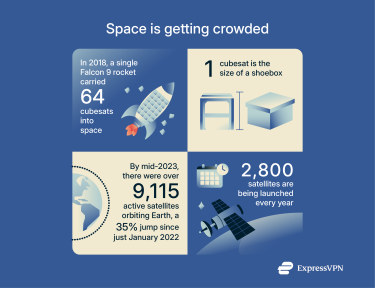
With an average of around 2,800 satellites being launched every year now, space infrastructure is denser and more interconnected than ever. This sheer scale means a single vulnerability in a popular satellite platform or a widely used ground software system could impact many satellites or millions of users at once. More satellites also mean more ground stations, user terminals, and networks: in short, a vastly expanded attack surface.
How everyday life depends on space systems
It’s not just astronauts or military officials who rely on satellites; it’s all of us, often in invisible ways. Global navigation satellite systems (GNSS) provide nanosecond-level timing that underpins stock exchanges and power-grid switches. Weather satellites feed disaster-response teams, while remote-sensing images guide insurers after floods.
Communications satellites deliver internet, phone, and TV service, especially in remote areas, on airplanes, and on ships. Imaging satellites support everything from Google Maps to humanitarian relief efforts. Our economy and safety are entwined with these space-based services, which is why they are considered critical infrastructure.
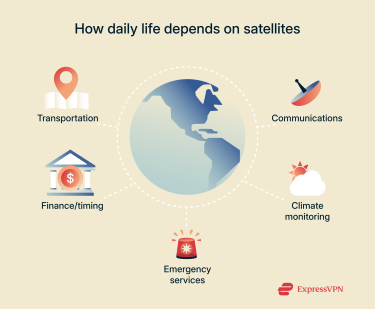
If cybercriminals were to disrupt or manipulate them, the effects could cascade across finance, transportation, energy, and more.
Key cybersecurity threats to space systems
As mentioned above, cyber threats to space systems span multiple segments, from orbiting satellites (space segment) and their communication links to ground stations and user equipment. Each segment (space, link, ground, user) presents unique openings for threat actors to exploit.
Jamming, hijacking, and exploitation risks
| Threat | What it looks like | Impact |
| Jamming | Attackers can interfere with satellite signals, blocking communication or navigation services. | It can cause outages or degrade service quality. |
| Spoofing/hijack | Unauthorized access to satellite control systems allows attackers to take over satellites. This can include sending false telemetry or command signals or spoofing GNSS signals. | This can lead to changes in satellite operations, data theft, or even physical damage by altering orbits. |
| Firmware tamper | Attackers slip malicious code into an over-the-air update. | Long-term backdoor or full payload loss. |
| Supply-chain malware | A DevOps plug-in imports a tainted library. The global and complex nature of aerospace manufacturing introduces many points where such compromises can occur. | Buried exploit activates after launch. |
| Data exploitation | Satellites and ground stations handle sensitive data that attackers can intercept or exploit. | Information can be stolen or operations spied on. |
Who is behind space cyber threats?
Potential adversaries range from nation-state intelligence units to lone hackers. Here are the main categories:
State actors
These are government-backed groups with extensive resources and strategic motivations. They may target satellites to disrupt military operations, spy on rivals, or compromise critical infrastructure. For example, attacks may focus on jamming satellite signals, injecting malicious code during software updates, or intercepting sensitive communications.
Cybercriminals
Traditionally motivated by profit, cybercriminals are beginning to eye space assets as valuable targets. They might attempt ransomware attacks on satellite operators or threaten to disrupt services unless paid. As commercial reliance on satellite-based services grows, so does the potential for financial extortion.
Hacktivists
These ideologically driven attackers may breach or disable satellite systems to make political statements or protest certain activities, such as surveillance or military operations. Although they typically lack the resources of state actors, their actions can still cause serious disruption.
The mix of motives means you face both stealthy spies and smash-and-grab crews. Planning must cover the full spectrum, from disruptive jamming to slow data exfiltration.
Understanding vulnerabilities in space technology
Satellites are no longer simple radio beacons. Inside each one sits a mini-data center running familiar technologies such as Linux, Docker, and over-the-air updates. That flexibility is great for new services, but it also imports the same weaknesses we fight on Earth.
Today’s “New Space” companies often move fast, using off-the-shelf parts and open-source software to cut costs and speed up launches. But that can come at the expense of proper security checks. Older “Old Space” satellites aren’t safe either: many were built before cybersecurity was a major concern.
Software updates = double-edged sword
Modern satellites are controlled by software that can be updated from Earth. That’s powerful, but risky. Rushed development can lead to missed bugs and weak security, while remote updates mean a single bad update could compromise many satellites at once.
Some satellites in orbit today still lack basic cybersecurity protections. If attackers sneak malicious code into an update, they could take over multiple satellites and the services they support, like hospitals, airlines, or emergency responders.
Ground stations are even easier targets
Satellite control centers use regular computer networks, making them vulnerable to:
- Malware
- Phishing
- Insider threats
- Network hacks
Instead of hacking a satellite directly, an attacker might just trick a ground station employee and slip in malware during the next satellite check-in.
Conclusion: Space is becoming a cybersecurity priority
As satellites take on bigger roles in communication, navigation, weather monitoring, and emergency response, cybersecurity has become an important part of space system design and operation.
The U.S. leans on the National Institute of Standards and Technology (NIST) Cybersecurity Framework, a flexible playbook originally made for critical infrastructure on Earth. It’s now being adapted to space through publications like NISTIR 8270, which applies cybersecurity principles to satellite vehicles, and NISTIR 8401, which focuses on satellite command and control, helping agencies map out threats, lock down systems, detect intrusions, and bounce back fast if something goes wrong.
And the job doesn’t stop with just launching the hardware. Modern satellites are software-driven and constantly updated from Earth, which means security has to be baked in from day one. U.S. policy now requires space systems to follow “security by design” principles, like encrypting commands, isolating ground systems, guarding against spoofing and jamming, and keeping a close watch on every link in the supply chain.
Europe’s also stepping up. The EU has passed new laws, such as the Network and Information Security Directive 2 (NIS2 Directive) and the Cyber Resilience Act, which treat space tech as essential infrastructure. That means stricter rules on incident reporting, testing, and software security, not just at launch but throughout a satellite’s entire lifespan. They’ve also launched the European Union Space Information Sharing and Analysis Center (EU Space ISAC), a hub where space agencies and companies share threat intel and respond to attacks together.
On the global stage, things are more complicated. International efforts to create shared rules, like those led by the United Nations, often move slowly, caught up in politics and clashing national interests. But progress is happening. Standards bodies like the International Organization for Standardization (ISO)’s Technical Committee 20/Subcommittee 14 (TC20/SC14) and Consultative Committee for Space Data Systems (CCSDS) are hard at work developing technical guidelines for space cybersecurity.
Bottom line? The race to secure space is on. And the smarter we get about defending it now, the safer life will be down here on Earth.
FAQ: Common questions about space cybersecurity
Who is responsible for protecting satellites?
Protecting satellites is a joint effort involving multiple stakeholders. Commercial satellite operators bear primary responsibility for securing their systems, including ground stations and communication links. They implement encryption and continuous monitoring and adhere to international cybersecurity standards.
Government agencies and regulatory bodies also have a crucial role, establishing and enforcing cybersecurity standards and policies. Organizations like the National Aeronautics and Space Administration (NASA) and the United States Space Force (USSF) protect governmental and military satellites, while entities such as the European Union Space Information Sharing and Analysis Center (EU Space ISAC) help coordinate global responses, ensuring intelligence sharing and collaboration against cyber threats affecting critical space infrastructure worldwide.
How are commercial satellites secured?
Commercial satellites employ multiple cybersecurity strategies to maintain security. They use robust encryption for both data transmission and storage, ensuring sensitive information remains confidential. Operators monitor satellites continuously, looking for signs of unauthorized access or abnormal behavior, allowing for rapid response.
Ground stations are secured through advanced network defenses, authentication protocols, and strict access controls. Many satellite companies follow guidelines like the National Institute of Standards and Technology (NIST) Cybersecurity Framework and collaborate closely with cybersecurity experts to regularly update and patch vulnerabilities.
What are the biggest cyber threats to space systems?
Space systems face several significant cyber threats, including signal jamming, hijacking, and exploitation. Jamming interferes with satellite signals, disrupting critical communications like navigation or emergency services. Hijacking involves attackers gaining control of satellites, potentially redirecting or shutting down vital services.
Ground stations remain vulnerable to cyberattacks, offering attackers an easier entry point to infiltrate space networks. Increasingly sophisticated state-sponsored hackers and organized cybercriminals constantly seek new vulnerabilities.
How does NASA address cybersecurity in space missions?
The National Aeronautics and Space Administration (NASA) implements rigorous cybersecurity protocols across all space missions. They use comprehensive threat modeling and cyber risk assessments to identify and mitigate vulnerabilities early in the design stage. Every mission incorporates encryption standards and secure communication protocols, protecting data integrity both onboard spacecraft and in ground communication links.
NASA continuously monitors systems, responding rapidly to anomalies. They actively participate in cybersecurity exercises, working closely with partners like the United States Space Force (USSF) and international agencies. NASA also prioritizes ongoing cybersecurity training for personnel, ensuring preparedness against the latest cyber threats and vulnerabilities.
What role does the U.S. Space Force play in cybersecurity?
The United States Space Force (USSF) actively monitors and analyzes potential threats to satellites, communication systems, and other critical assets. This includes managing cybersecurity for military communications and GPS satellites vital to national security.
The USSF conducts threat intelligence gathering, cyber defense operations, and incident response. It also develops advanced cybersecurity strategies and technologies, ensuring readiness against emerging cyber threats.
What is the role of AI in space cybersecurity?
AI plays a big role in protecting space systems from cyber threats. It can quickly scan massive amounts of data from satellites and networks, spotting strange patterns or unusual behavior that might mean a cyberattack is happening.
AI also helps by automatically adjusting defenses as new threats appear, reducing the need for constant human monitoring. On top of that, it can use predictive analytics to guess what kinds of attacks might come next, giving security teams a chance to prepare in advance.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN