-

Weighing up the morality of internet privacy
The difference between right and wrong is rarely black and white. When it comes to the big moral issues around internet privacy—from government surveillance to Facebook privacy—you might have your...
-

How plausible deniability can protect your data
Plausible deniability allows individuals to claim they had no involvement in an action taken by others (or, in some cases, themselves). For example, though you can plausibly state that you do not know...
-

Is internet privacy a lost cause?
Most people think of privacy as a fundamental right. The right to have a personal conversation without someone listening, the right to keep your belongings out of public view. ExpressVPN believes that...
-

Am I being spied on? Here's how you might be
Are you being spied on online? The short answer is: probably. This post will take a look at the key ways third parties could be snooping on your online activities right now. Government surveillance Yo...
-

How to properly dispose of your hard drives
Data is valuable. Your pictures, legal documents, chat logs, and even saved video games are all things you wouldn't want to be public. Today, people generally go to great lengths to protect data, but ...
-

Why encryption is vital in free societies
In 2011, the United Nations declared internet access a universal human right. That was a necessary step forward for digital freedom, but it’s far from sufficient—it needs to add encryption to the ...
-
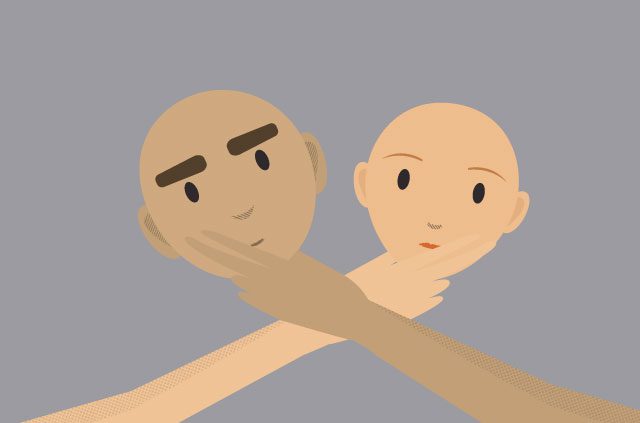
Facial swapping software is now open-source
Developed by experts from the Massachusetts Institute of Technology and NVIDIA, vid2vid technology allows anybody to swap the surface images of objects in a video. Most of us know this kind of video-t...
-

The art of social engineering: Are you being conditioned?
As we get better at securing our computer systems, we are discovering that the weakest line of defense is, in fact, the human being. Social engineering is the dark art of manipulating people. Social h...
-

4 ways the CIA can hack you right now
Five years ago, Edward Snowden revealed that the NSA extensively collects information on citizens worldwide. It’s now clear that privacy is no longer a right we can take for granted. What’s more, ...
-

Eight women in Bitcoin you should follow on Twitter
The old cliche that there are few women in Bitcoin is getting a bit tiring. Plenty of women contribute to the technology, community, and investment side of what we consider one of the most exciting hu...
